Hi All,
I have a Juniper SRX 210 that I have many VPN tunnels terminating too, these are all juniper to juniper. I have the need at the moment for a user to connect in via Billion modem, it has do IPSec Tunnelling and I'm trying to set it up, but I keep getting an error no proposal chosen. I would love a sanity check to see what I might be doing wrong here.
Juniper snippet of config,
set interfaces st0 unit 20 description "VPN Interface to CCA"
set interfaces st0 unit 20 family inet
set routing-options static route 172.22.110.0/24 next-hop st0.20
set security ike proposal ike-proposal authentication-method pre-shared-keys
set security ike proposal ike-proposal dh-group group2
set security ike proposal ike-proposal authentication-algorithm sha1
set security ike proposal ike-proposal encryption-algorithm 3des-cbc
set security ike proposal ike-proposal lifetime-seconds 28800
set security ike policy ike-policy-backup mode aggressive
set security ike policy ike-policy-backup proposals ike-proposal
set security ike policy ike-policy-backup pre-shared-key ascii-text "xxxxxx"
set security ike gateway CCA ike-policy ike-policy-backup
set security ike gateway CCA dynamic user-at-hostname "cca@xxxx.com"
set security ike gateway CCA no-nat-traversal
set security ike gateway CCA local-identity inet xxx.xxx.xxx.xxx
set security ike gateway CCA external-interface ge-0/0/0.0
set security ipsec proposal ipsec-proposal protocol esp
set security ipsec proposal ipsec-proposal authentication-algorithm hmac-sha1-96
set security ipsec proposal ipsec-proposal encryption-algorithm 3des-cbc
set security ipsec proposal ipsec-proposal lifetime-seconds 3600
set security ipsec policy ipsec-policy perfect-forward-secrecy keys group2
set security ipsec policy ipsec-policy proposals ipsec-proposal
set security ipsec vpn vpn-to-CCA bind-interface st0.20
set security ipsec vpn vpn-to-CCA ike gateway CCA
set security ipsec vpn vpn-to-CCA ike proxy-identity local 172.25.199.0/24
set security ipsec vpn vpn-to-CCA ike proxy-identity remote 172.22.110.0/24
set security ipsec vpn vpn-to-CCA ike ipsec-policy ipsec-policy
set security ipsec vpn vpn-to-CCA establish-tunnels immediately
set security zones security-zone untrust interfaces st0.20 host-inbound-traffic system-services all
Picture of the Billion config is attached.
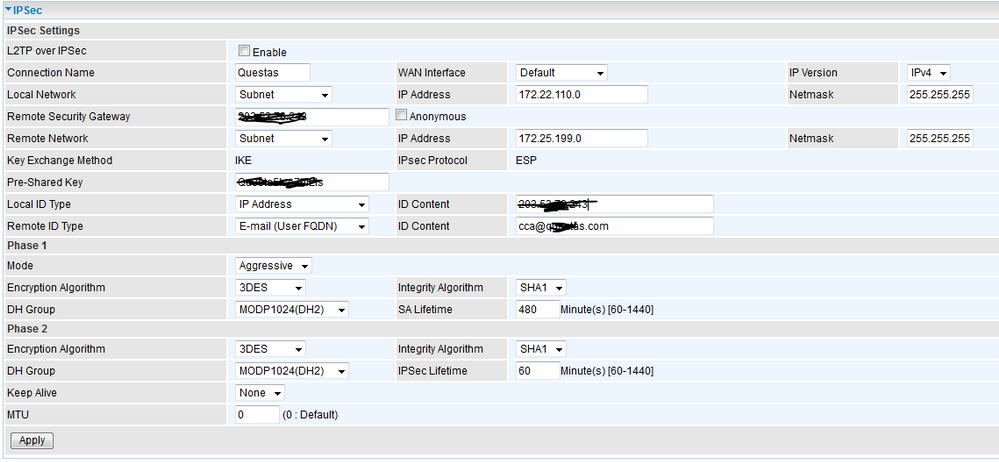
In the above, the Remote Security G/W is the public IP on the Juniper SRX and the local ID type IP address is the ike gateway CCA local-identity inet address.
Thanks everyone in advance.
Cheers, Jason