Hey guys,
it's been a while, but I'm getting back into my networking stuff. So I have a little bit of a dilemma.
Here is what I want to accomplish on my network:
Basically, I'm looking at creating two LANs (seperate networks). One for testing and the other is a live network.
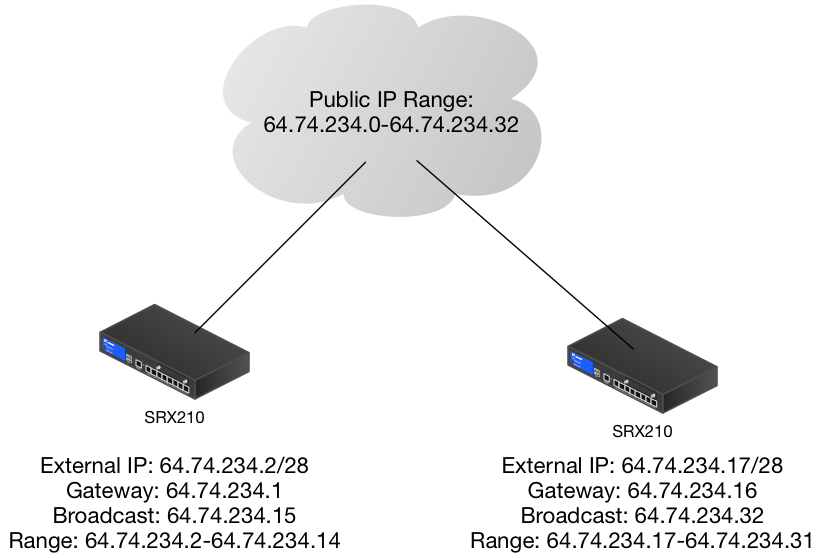
Our ISP gave us 32 public IP addresses (altered here for security reasons):
64.74.234.0-64.74.234.32
We want to use the first 16 IP addresses for our live network, and the last 16 IP addresses for a test network. The problem is, the first network works.
It's configuration is 64.74.234.2/28, the route (gateway) being 64.74.234.1.
The second network however, does not route out. Whenever I try to ping out, I get the following response:
ping: sendto: No route to host
Being that I'm a networking noob, I was under the assumption that 64.74.234.17/28 would route out through 64.74.234.16.
Any idea what I'm doing wrong here?
For what it's worth, my NAT configuration and policies all check out, but I'll post the config if necessary.
Thanks guys.
-Dave