Hello,
I've been tasked with setting up an IPSec tunnel to our new cloud VM service from one of our remote sites where we have an older Juniper SRX firewall. This is really my first time ever configuring a Juniper firewall, so I'm a bit lost in the CLI and details of it all and figured I might find help here.
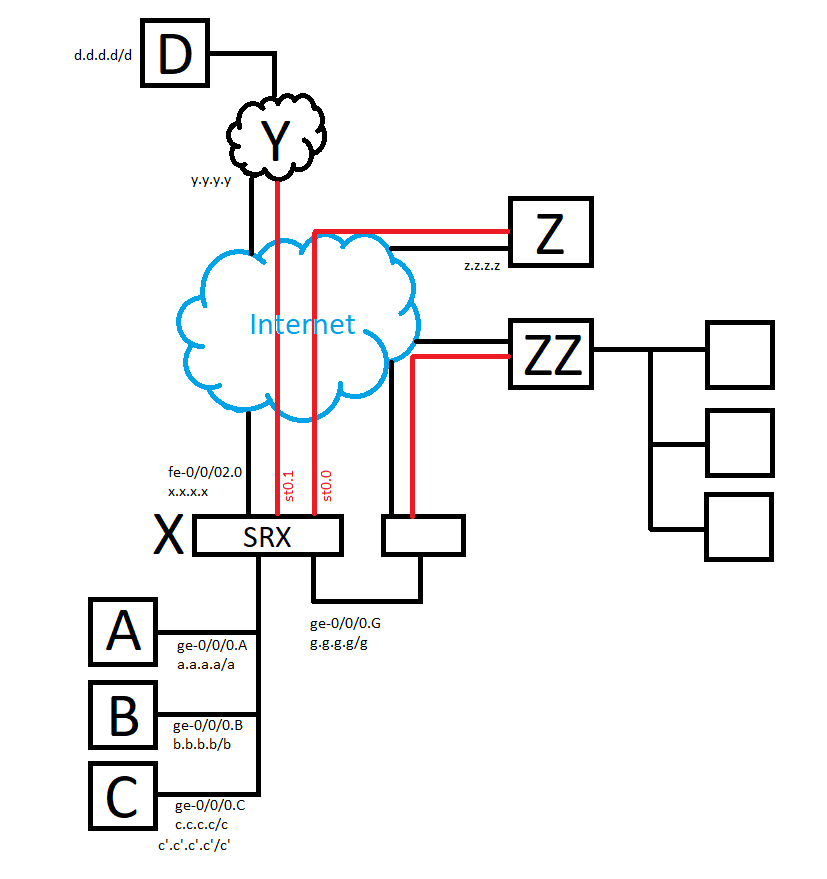
Anyway, as I've tried to describe in the attached image, our remote site X needs a tunnel for our subnets to our cloud service Y. Specifically the subnets on logical interfaces A and C on X to D on Y.
I have successfully set up a route based VPN on interface st0.1 that currently allows traffic between A and D, but I'm a bit stumped as to how I can get traffic between C and D as well. I had hoped it would be as simple as expanding the trust-to-VPN zone security policy address entries from A to [A C], but I guess something else is required?
If it is relevant, c.c.c.c/c is already routed to a separate VPN to a third party site Z on interface st0.0, and both A and C are routed to a separate physical device that provides a tunnel to a fourth site ZZ. These configurations need to stay.
A, B and C are all part of the trust zone, st0.0 and st0.1 each belong to separate VPN zones. There is a further smattering of interfaces and subnets, but I hope they shouldn't be relevant for this.
 Routing overview
Routing overview