Today organizations need to be prepared for a number of different types of DDoS attacks on their networks. Juniper Networks announced several new enhancements that allows its DDoS Secure solution to help the network better defend itself by using routers as enforcement points.
DDoS Attacks on the Rise
In the case of volumetric attacks that have the potential to flood the pipe capacity and overwhelm the edge equipment and the protected resources behind it, it’s important to handle it at the router, closer to the attack source. If an attack can be accurately detected at the edge, and then communicated to the upstream routing infrastructure, companies are able to effectively block bad traffic close to the source without disrupting normal service, delivering the desired results. This strategy is most effective not only for mitigating Distributed Denial of Service (DDoS) attacks, but also for ensuring DNS availability.
However, volumetric attacks are only part of the problem. Targeted DNS-based attacks are also of significant concern to enterprises and service providers alike. There are now multiple ways attackers could abuse DNS to take down networks. Consider a service provider’s core DNS infrastructure. A DNS amplification/reflection attack where the DNS infrastructure participates in the attack, or a consumption attack where the DNS infrastructure itself comes under attack, can bring the network operation to a halt with serious revenue implications. For instance, when the attack amplifies to 100’s of gigabytes as we saw with the Spamhaus and NTP amplification attacks earlier this year, then the only course of remediation is to block upstream.
The Network Defending Itself Against DDoS
Mitigating DNS attacks requires a holistic approach. While detection of such attacks will occur on-premises at the network edge, again more effective mitigation must occur upstream at the router. The farther away from the network boundary the better. It’s this one-two punch that is most effective against DNS amplification and reflection attacks.
But how is that possible? Border Gateway Protocol (BGP) Flowspec is a standard routing protocol that provides a mechanism for mitigating DDoS attacks in the routing infrastructure if properly integrated with an on-premise DDoS solution. The granular capabilities of BGP Flowspec not only can deliver clean pipes downstream to the enterprise or data center, but it also stops malicious traffic as close to the attack source as possible. The granularity of Flowspec allows the operator to get rid of only the bad traffic upstream before it hits the link, without the need to divert all the traffic to a scrubbing center.
Juniper’s Approach
Juniper’s MX routers are BGP-enabled, providing the ideal complement to DDoS Secure, Juniper’s on-premise, heuristics-based DDoS protection solution that now delivers support for BGP Flowspec. This integration of DDoS Secure and the MX via BGP Flowspec extends the application layer protection at the premises to include upstream mitigation of larger attacks. This combined effect of heuristics-based intelligence and granular attack filtering rules for upstream enforcement by the MX keeps the network free of attack traffic without disruption to normal service and keeps operational intervention to a minimum.
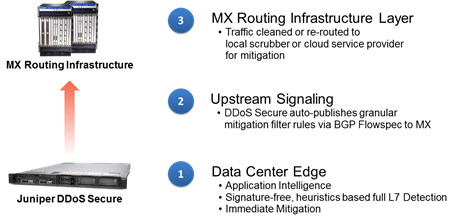
Juniper’s DDoS Secure is the only solution to both utilize heuristics-based detection of DNS attacks and combine mitigation with upstream MX routers for granular, efficient and distributed protection close to the source of the attack. Extending mitigation filters to the network border establishes an ability to deal with very large DDoS attacks that threaten the network availability of a critical service such as DNS. All DDoS attacks, whether DNS-based or otherwise, are addressed using this combined on-premises and network approach for detection and mitigation.