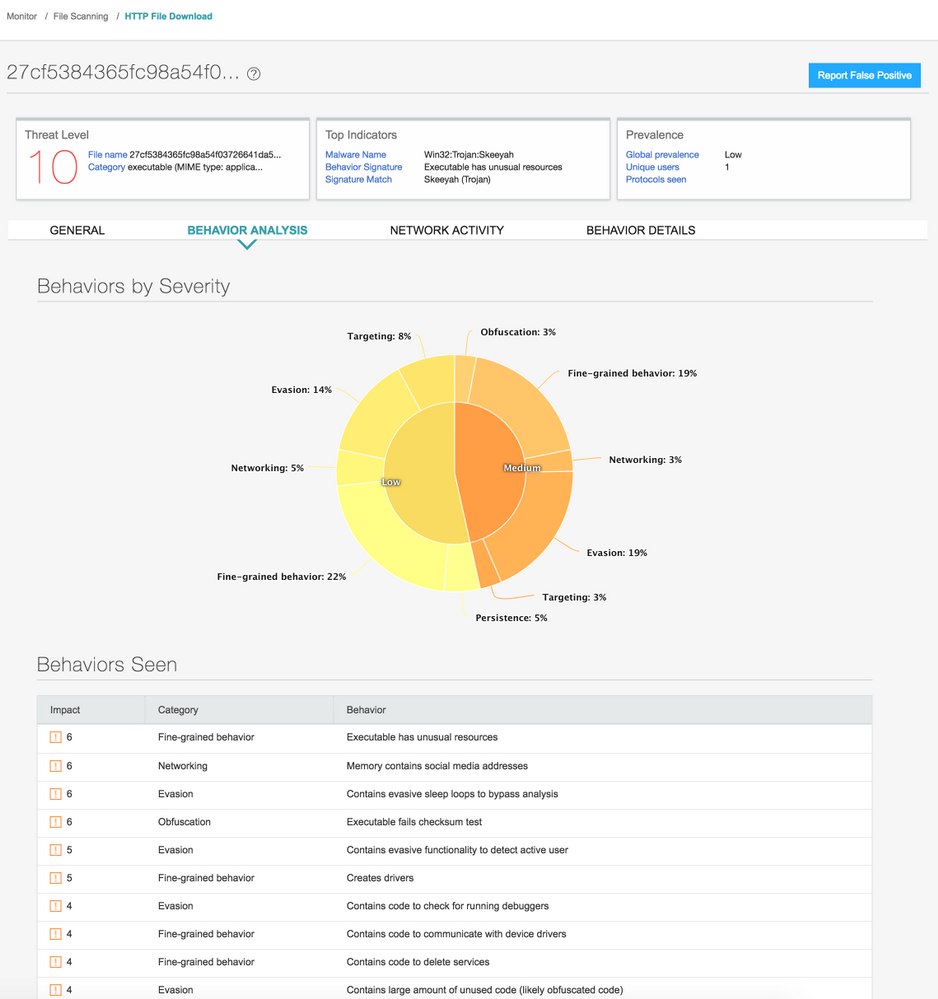
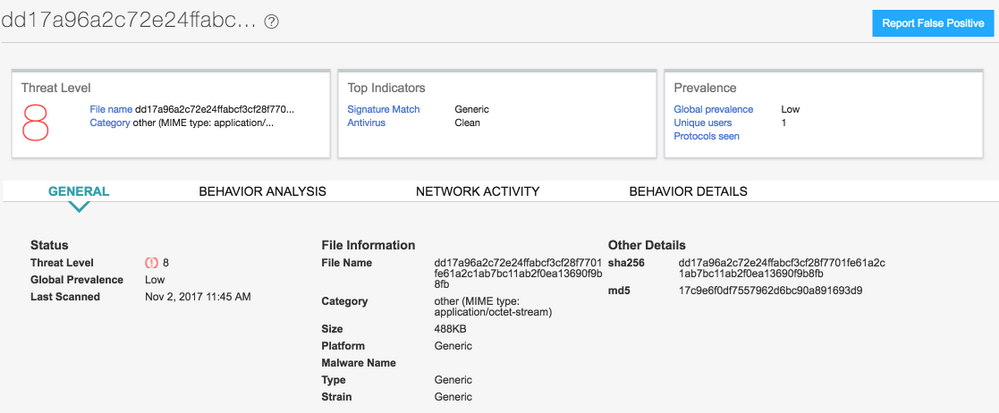
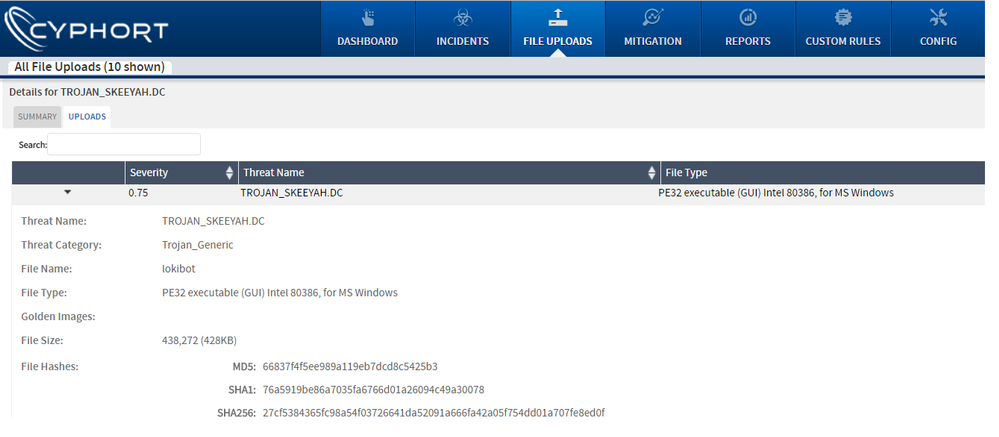
Introduction
We recently detected a Lokibot sample that was delivered as an email attachment to one of our customers in the healthcare vertical. Below is the technical analysis of the sample.
LokiBot is an infostealer that is known to steal various kinds of data like ftp credentials, email clients passwords, passwords stored in the browser, etc. Lokibot is distributed in phishing emails and known to exfiltrate data using the POST method over http.
Indicators of Compromise
- iso file :
- Md5: 17c9e6f0df7557962d6bc90a891693d9
- Sha1: 2ee42a051823b4e1bc0ed643c0b15843cce7c056
- filename: Proforma Invoice pdf.exe
- Md5: 66837f4f5ee989a119eb7dcd8c5425b3
- Sha1: 76a5919be86a7035fa6766d01a26094c49a30078
- Unpacked:
- Md5: 9335ce514bbdd9d146f30970569be44f
- Sha1: 06aacbc54f93afcf29e3ee7966e236d7d9b98e60
- .hdb file found in appdata
- Connects to URLs that end with fre.php
Technical Analysis
The file is packed with a VB-compiled packer which usually makes the reversing tougher.
Additionally, this sample uses anti-debug techniques and runpe which makes it harder to reverse engineer.
The obfuscated code decrypts to a virtually allocated memory by pushing to stack and then popping and xoring the data:
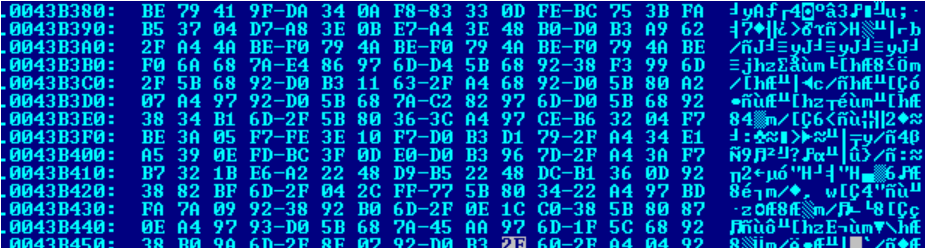
Fig: Obfuscated code in the file
The obfuscated code is copied to memory using a sequence of push and pop created in reverse order.The content can be decrypted with the xor key 0x5BD09268.
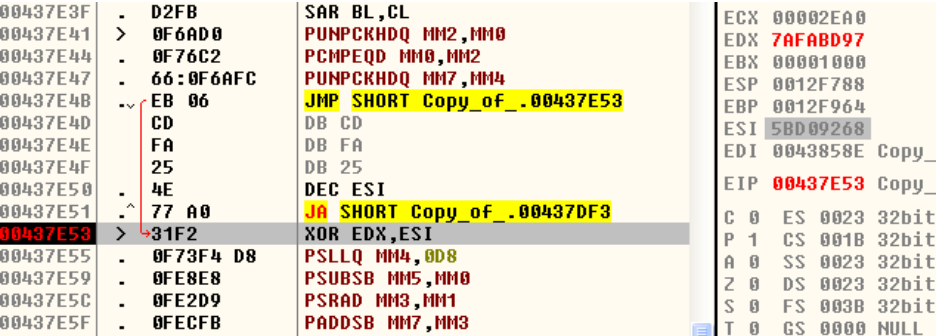
Fig: Decryption loop
Anti-debugging
The malware then jumps to the decrypted code. First it checks for anti-debug techniques. If a debugger present it jumps to a code which throws an exception.
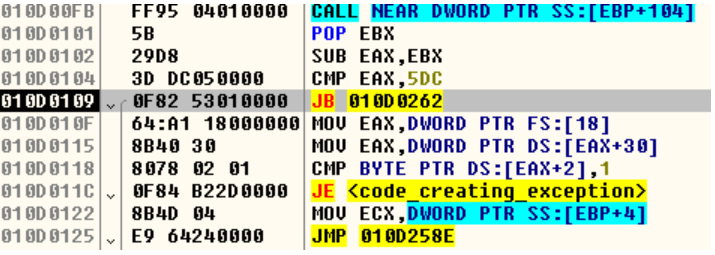
Fig:Checks BeingDebugged falg in PEB
Sandbox detection code:
The above code detects a sandbox by saving the CurCursorPos then sleeping for a second and then comparing the cursor position to its previously known location. If it is the same, the malware throws an exception.
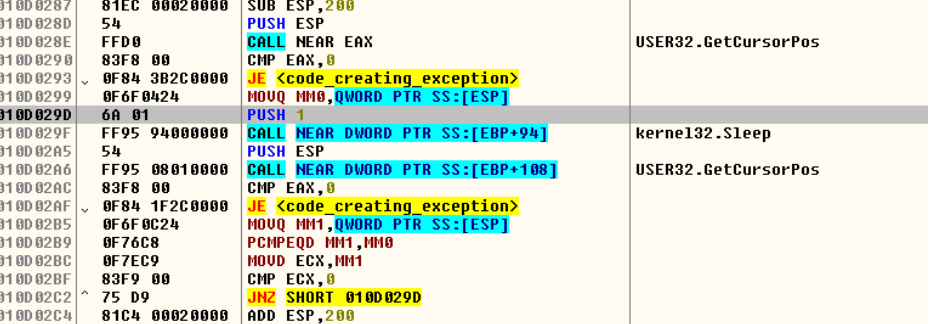
Fig: sandbox Detection
Other anti-debug checks
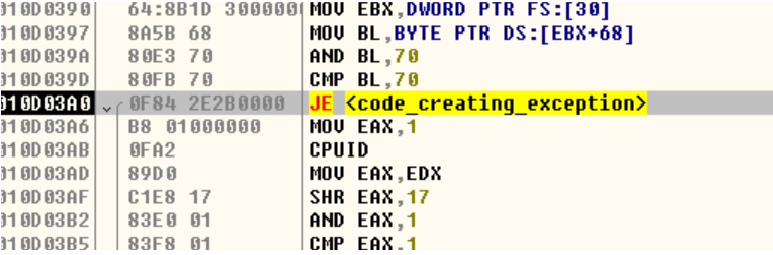
Fig: Checks for NtGlobalFlag in PEB for debugger detection
When satisfied it is not being monitored, the malware uses process hollowing to inject a payload into its own newly created suspended process.
Unpacked sample:
After unpacking, we can identify a lot of strings in the malware. The malware strings look similar to the strings observed in LokiBot.
The malware checks for the presence for various configs, settings files for ftp, browsers, email clients with hopes it can steal their credentials.
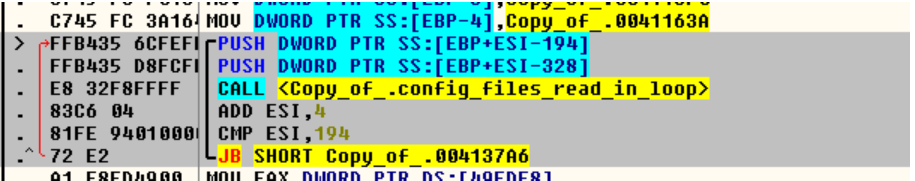
Fig:Reads config files of of various softwares in loop
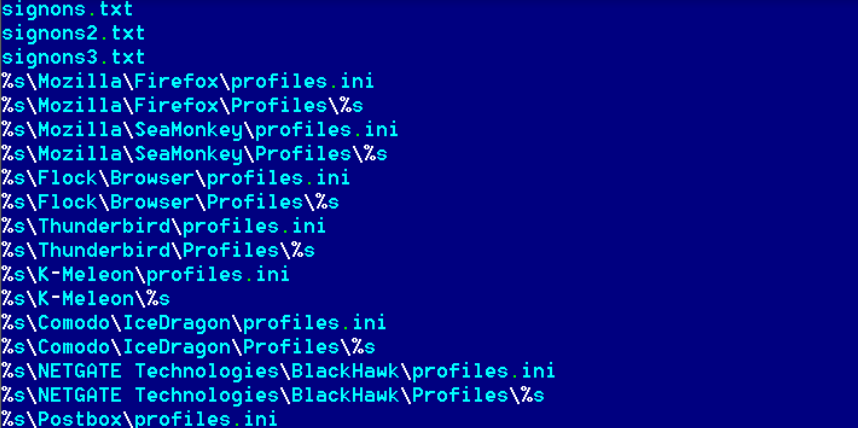
Fig:config files of various softwares
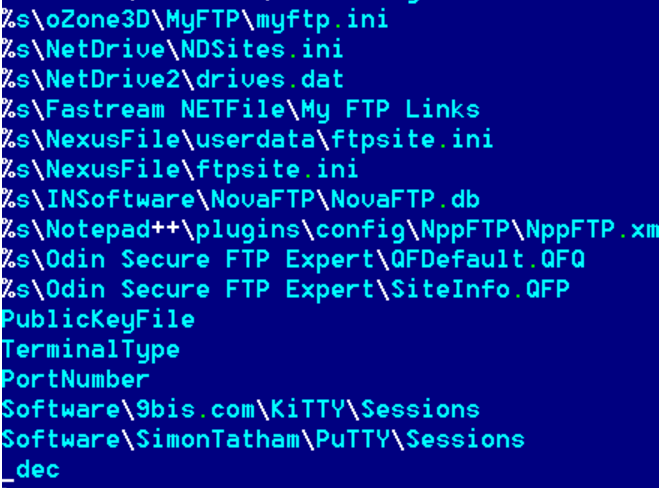
Fig:List of FTP files
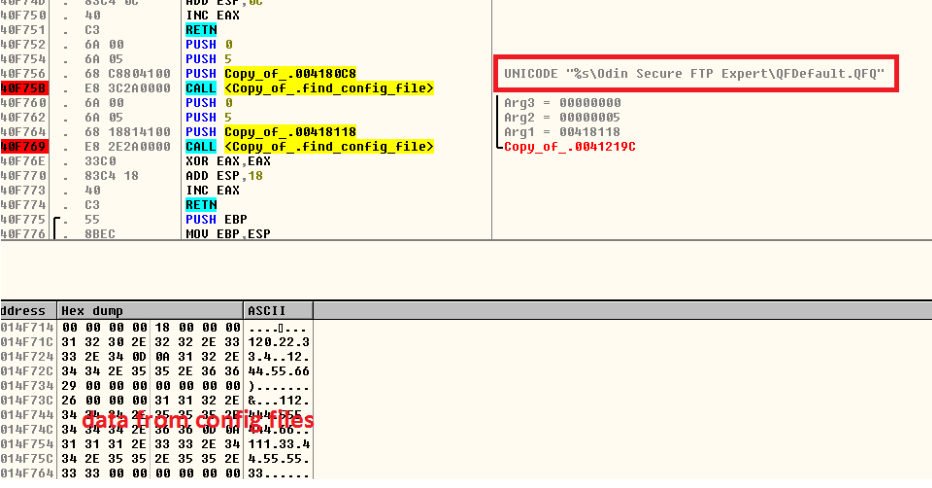
Fig: malware reads config files of Secure FTP Expert
A .hdb is created in appdata folder which indicates the presence of lokiBot . This file seems to be some kind of database used by the malware. This can be used as IOC for LokiBot.
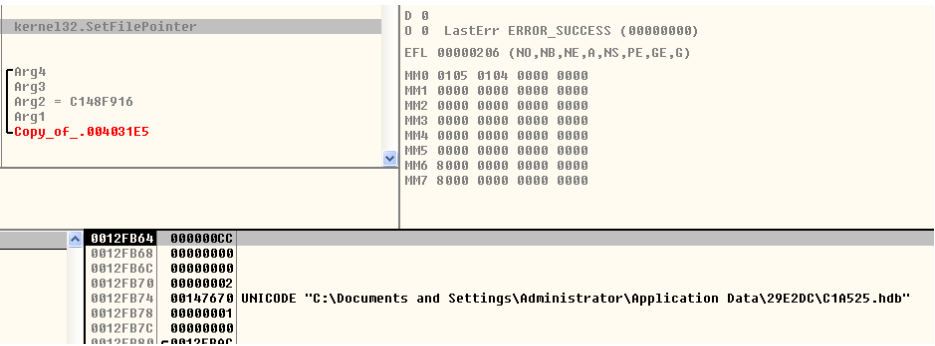
LokiBot is known to compress this data before sending it to the CnC server.
The malware uses an http POST method to send the stolen data to the CnC server.
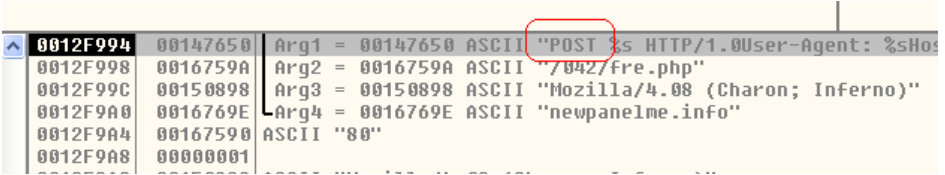
Fig: LokiBot sends data to CnC server
CnC:
The sample connects to following URL and sends the stolen data:
http://newpanelme.info/042/fre[.]php
These C&C URLs usually end with fre.php
Here are a few more URLs used for the same purpose, discovered by other security vendors
- southeasterncontractingco.com/AM/G00gle/fre[.]php
- axpired.xyz/013/fre[.]php
- 154.16.49.153/loved/know/fre[.]php
- toopolex.com/controllers/user/fre[.]php
Detection
Both Juniper Sky ATP and Cyphort(now a Juniper company) on-prem solutions detect this threat as seen in the screenshots below: