In his keynote speech during the RSA conference of 2011, the former director of the NSA, Gen. Keith B. Alexander made an interesting statement: “Securing our nation’s network is a team sport”. It is cleared now than ever, that no-one can fight the cyber war alone, and community efforts sharing cyber threat intelligence could benefit all participants, even in a competitive environment.
When referring to modern cyber threats, the attackers seem to have the upper hand. Regardless of their motivation, their engagement with the target has many asymmetric characteristics which work in their benefit, creating the need for new defense concepts deployed is a seemingly never ending arms race.
One of those new concepts is the sharing of real-time actionable cyber threat intelligence (CTI) - the exchange of dynamic feed of threat or attack related objects utilized for enforcement or analysis at the receiving end. Sharing CTI between different organizations, represents a collaborative effort to improve cyber defense posture by leveraging the capabilities, knowledge, and experience of the broader community. Such deployments may take different technological and structural forms, eventually reducing duplication of effort while enabling one organization’s detection to become another organization’s prevention.
In recent years, a growing number of sharing alliances have emerged, either between individuals using social networks, within the same vertical market, across different sectors in the same geography, between commercial and government bodies, and even among countries. In many cases these sharing initiatives represent a shift in the organization’s legacy IT paradigm, and create a complex, multifaceted challenge to technology, law, organizational culture, privacy and more[1]. These challenges are bigger when the parties are direct competitors or have other conflicts of interests, as demonstrated in my research-in-progress conducted at the Blavatnik Interdisciplinary Cyber Research Center (ICRC). The research analyzes threat intelligence sharing between cybersecurity vendors, with the goal to create visibility and understanding of the formed ecosystem within this industry. Since the shared information is closely related to the core business of the firms, it presents clearly the challenge of combining collaboration with competition named as coopetition.
Security vendors have already embraced CTI as a defense concept providing their customers with a viable solution, but the disaggregation of the solution elements described in Figure 1, allows them to mutually use feeds from each other, or provide their threat intelligence using another vendor as a sales through channel. These three elements may belong to one or several vendors, and deployed as a single or multiple products either on customer premises or in the cloud. The source point of the information flow is a threat intelligence feed, and the destination is a policy enforcement or decision point. In between, an optional element called Threat Intelligence Platform (TIP) may act as an exchange point tying several sources and destinations together. Integration between all elements is based on either proprietary API’s or evolving standards such as STIX™, TAXII™, and CyBOX™.
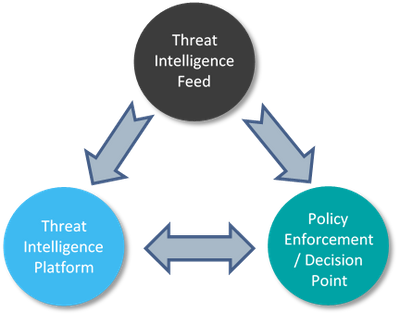 Figure 1 – Disaggregated elements of threat intelligence sharingThe key findings of the research suggest that cooperating with competitors is a winning strategy, showing correlation between market-related success indicators of a vendor, to its number of sharing relationships. Furthermore, the industry as a whole is a coopetition fit environment divided into social network communities, where successful companies attract new relationships more, following the ”rich-gets-richer” phenomenon. In addition, intelligence sharing can result in better security coverage, direct and indirect financial gains, and benefit to the greater good.
Figure 1 – Disaggregated elements of threat intelligence sharingThe key findings of the research suggest that cooperating with competitors is a winning strategy, showing correlation between market-related success indicators of a vendor, to its number of sharing relationships. Furthermore, the industry as a whole is a coopetition fit environment divided into social network communities, where successful companies attract new relationships more, following the ”rich-gets-richer” phenomenon. In addition, intelligence sharing can result in better security coverage, direct and indirect financial gains, and benefit to the greater good.
Given the possible advantages to companies, and the challenge of fighting the cyber war alone, many organizations are reconsidering their policy on sharing cyber related information with outside parties, literally demonstrating that crowd wisdom is applicable in the cybersecurity domain. For more on the topic from both academic and industry perspectives, join my presentation “101 to Threat intelligence Sharing”, at the (ISC)² Security Congress EMEA in Dublin 18-19 October 2016, or at the CSX 2016 Europe conference in London 31 October-2 November 2016.
[1] Zrahia, A. (2014). A multidisciplinary analysis of cyber information sharing. Military and Strategic Affairs, 6(3), 59-77. E-ISSN 2307-8634. The Institute for National Security Studies (INSS), Tel-Aviv University.