According to recent security reports, botnets have become an increasing security concern, infecting tens of millions of computers, stealing users’ data, identities and helping to mount DDoS attacks. In fact, it has been estimated that up to a quarter of all personal computers participate in a botnet.
The most common examples of such malware are Zeus and its successor SpyEye.
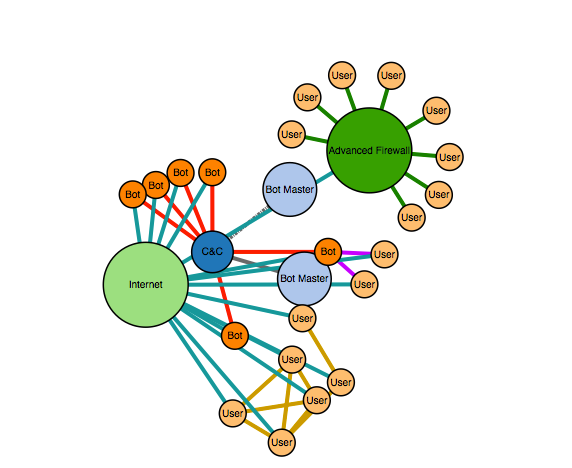
The chart above shows an example of a high level botnet architecture and a possible protection against it. Multiple botnet masters (light blue) can utilize the botnet C&C server. The principal botnet master has full access to the server (solid link), while customers of the service may only have access to a Web UI that lets them give predefined commands to the bots (dashed link).
The C&C server communicates with multiple previously infected users that are now bots (orange) and sends them directions. Users that exchange data with bots – be it via e-mail, network connection or USB sticks (purple links to yellow users) are in danger of being infected and controlled by the C&C server. The cluster of users that is not connected to the C&C server and isn’t behind an advanced firewall with anti-malware solutions is also in danger of being infected. As soon as one of them is infected, others in the cluster may have a higher chance of being infected. Finally, a cluster of users behind the firewall are not likely to be infected by the botnet.
Another possible architecture shown below is a p2p botnet like a recently released GameOver Zeus.
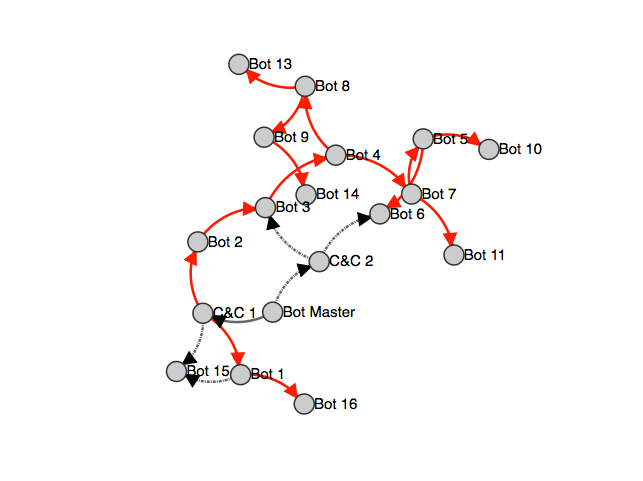
There may be multiple C&C servers that can give commands to nodes that further propagate these commands. Propagated commands are in red. Failed commands are dashed. Direct commands are in black solid. Even a loss of a C&C server (C&C 2 in this case, whose commands always fail) allows the system to recover. Additionally, tracing the location of the C&C server may be difficult, because it may not issue commands to the bots directly.
The birth of a botnet (Can you create your own botnet?)
To create a botnet, the botnet master needs to infect computers with malware. This can happen in multiple ways. Examples include inserting an infected USB drive into a vulnerable machine, having users visit an infected website that hosts a dropper, installing pirated software that is pre-infected with malware or via email phishing campaigns.
Perhaps surprisingly, botnets are sold freely on the open internet.
To own a botnet, a bot master needs five things:
1. Leased hardware to host the C&C server and a VPN service to protect the server IP. The bot master can connect to this server and issue commands to bots in the botnet.
2. The C&C server software. This could be existing open source botnet that would be detected with most AVs or a new, yet undetected botnet that can cost up to $40000.
3. Exploit. This is a method to put the malware on the machine of the victim. It is usually a script located on a malicious site that exploits the browser of the victim to have the victim download and execute the malware. It could either be free for some old vulnerability in an old browser or up to $250k for a 0-day.
4. Traffic. Here the bot master pays for the users to visit the site that hosts malware. It could be a bribe to owners of a popular site, a payment to borderline illegal sites such as sites hosting torrents, or a payment to hackers that found a vulnerability in a website. An example of the latter is WinZip homepage that was recently temporarily compromised.
5. Work. This is a payment to a software engineer to connect these pieces together. This person must configure the C&C server, link it to the infected machines and set up a system where new machines are infected. Usually this service is sold along with the exploit or performed by the bot master himself so it won’t cost anything extra.
Some of these services can be combined together. For example, one can buy traffic/exploit together or simply rent a functional existing botnet with all of these pieces in place and user-level access to a C&C server via Web UI.
Where are they sold and how much does it cost?
| Service |
Price ($) |
| Hardware |
100 |
| Software |
0-40k |
| Exploit |
0-250k |
| Traffic |
0-5k |
| Work |
0-1k |
All of these services could be found on Russian sites that came up with a simple google search:
http://cheat-master.net/
 Screenshot from a post on cheat-master site.
Screenshot from a post on cheat-master site.
http://prologic.su
 Screenshot from a post on prologic site.
Screenshot from a post on prologic site.
Here, the first link sells/rents out a DDoS botnet, and the second shows someone listing an installation of arbitrary software on 1000 machines for ~$350 on USA and < $100 in Eastern Europe/South America.
So how much does it cost in total?
For a big USA-based botnet with custom software and zero-day exploit it could cost up to $300k as we calculated above. A botnet with users in Brazil could be had for the price of a server and $85 per 1000 users and ~$6k in total per month for a 65k user botnet. This botnet might be able to launch a 6.5Gbps attack.
However, if a cyber-criminal wants to simply perform a DDoS attack on an unprepared site, creating a new botnet might be overkill. A DDoS attack could cost just $5/hr
 DDoS service offered for $5 an hour by a “rated” user.
DDoS service offered for $5 an hour by a “rated” user.
Defense through economic infeasibility
One way to defend against these attacks is to make their execution too expensive to be considered an option.
There are two places where an economic defense is possible.
The first is preventing an existing botnet from being useful.
The second is preventing the establishment of a botnet in the first place, thus limiting not only DDoS attacks, but also credential and intellectual property theft.
To prevent an existing botnet from being useful, one needs to make every single use of it obsolete or too expensive compared to the cost of the botnet itself. Here we’ll go over how we can make it economically infeasible to use botnets for the currently used common purposes.
DDoS is perhaps the best known and the most dangerous use of a botnet to internet-based businesses. Incentives for DDoSing a site can be huge, as a DDoS attack could disrupt a competitor’s service for hours at a crucial time.
To prevent DDoS attacks, the site being attacked has to have infrastructure in place (or hire a firm that has that infrastructure) to defend against them. For example, according to data from CloudFlare to launch a 65Gbps attack (which is the amount of bandwidth one would need to bring down a medium-sized website) you’d need a botnet with at least 650,000 compromised machines. If this is the case, 1000 attacking bots will not cut it. So a cyber-criminal would need to spend significantly more time finding new botnets to rent and pay them more and more to be able to mount an attack that would have a potential of shutting down a website.
So renting out a botnet for a small DDoS attack for $60/day would not have the desired effect. Looking for additional sources that have more machines available is challenging because of several issues:
1. Different people selling DDoS services online may be utilizing the same botnet. There is no way to confirm it until the price is paid or there is a preexisting relationship with botnet providers. Since there is an inherent lack of trust between criminals online, establishing this relationship may be difficult.
2. Each time the botnet customer buys the service, they risk having their payment stolen. On Russian cyber-criminal forums, DDoS providers who fail to deliver a service are banned and not trusted in the future, but it is very easy for them to create a new account and establish some initial positive feedback from customers with lower requirements.
The only way for a cyber-criminal to guarantee a heavy DDoS attack from tens of thousands of bots is to own the botnet themselves, and as we saw in the previous section, this can get very expensive quickly.
Spamming is another common use of a botnet. The only sure way to fight it is to detect spam as spam. Luckily with the help of recent advances in machine learning and their implementation in common email service providers, spamming seems to be declining.
Sniffing Traffic/Keylogging is a set if methods that capture user data from the computer the malware is installed on. The defense against these methods involves capturing/detecting malware before it does something malicious, blocking its communication with the remote C&C server, and notifying banks/user about credit card theft. A combination of these 3 defensive tactics could make it difficult to steal credentials this way.
Installing Advertisement Browser Addons. This is a major cash cow for malware authors because they get money when users click on ads that they display. Such attacks could be mitigated by preventing installation of addons that are known to be malicious by users or that communicate with known adware sites. This is essentially in-browser malware and can be dealt with using the same techniques used to deal with standalone malware.
Google AdSense-like service abuse. This is a technique for directing traffic at sites that the malware author hosts in order to profit from advertisement revenue. This could be dealt with by the companies hosting these services by not distributing rewards immediately to site owners that have suspicious network traffic activity coming from their visitors.
All of these strategies can only go so far, because the bot master essentially owns the machine that has the C&C-controlled malware installed and can use it for any purpose one could use computers for. It is, of course, better to not have many botnets to begin with.
This brings us to the second potential defense: preventing the establishment of a botnet. This can be done by breaking the chain of events necessary to create the botnet.
1. Server providers are penalized for renting out servers for C&C hosting. It is primarily done indirectly by putting the IPs of the C&C servers on blacklists, thus forbidding future legitimate customers from using the server infrastructure providers’ services. Increasing these penalties, such as requiring a payment for unbanning IPs would result in further revenue loss and therefore disincentivize these providers from renting out servers to known botnet masters.
2. Antivirus vendors quickly write signatures against common botnet software.
3. Chrome and Firefox offer bounties for bugs and exploiting browser vulnerabilities is becoming much more difficult. This defense is further bolstered by automatic browser updates that do not require user interaction and a smaller attack surface (discontinued Java applet support).
4. Google/Adblock can prevent users from visiting known malicious sites even if they were live for a short period of time.
5. Lucrative employment opportunities in developing countries in legitimate businesses through remote work leave few software engineers willing to take risks facilitating botnet proliferation.
Economic disincentives are only one approach at eradicating botnets. There are many ways to look at the problem. Among other potential solutions are required forced migration from older, unpatched systems, user education on safe browsing, and improvements in anti-malware and advanced firewall solutions.
Article also available at Juniper SecIntel blog.