When I wrote a blog about using a switch as security device in 2013, I couldn’t have predicted the attention it got. It might have been the fact that I publicly admitted to being aware of my mental state for writing about switches in a security oriented blog space. Or maybe it was the content of the blog after all. Anyway, I got a lot of comments and questions about that blog. So almost five years later my friend Valentijn pointed out to me that a small follow-up was needed. It seems at this point in time IPv6 is actually being used in LAN scenario’s instead of just WAN and 6 to 4 natting. This creates a new set of security risks we can address in the switch config without much effort. It’s just a matter of configuring a few features. It’s not my intention to rewrite a manual, I’ll just hyperlink to the existing documentation. Nor is it my intention to write a complete security implementation guide. Just read this when you work with IPV6 and get inspired to read more on this subject. One more disclaimer: I’m not going to explain IPV6 here. It’s 2018; you should at least understand the basics of IPV6 by now. The diagrams of course are Valentijn’s not mine. I have other strong points then playing with Visio…..
Stateless RA Guard
One way of working with dynamic address is using stateless auto configuration, SLAAC. When you do this a host sends a router Solicitation (I’m not allowed to call that a discovery, but if I do you understand immediately) and a router hands out an IP address. So far so good, but what if a rogue router is attached to switch? Clearly you see the analogy to a rogue DHCP server on an IPv4 network. Nothing good can come from that. This diagram should make clear what happens:

The RA guard feature helps prevent this. Ports with a valid router attached are marked as trusted. Only Router advertisements of routers on trusted ports can pass your switch. Information on how to configure this can be found here.
Stateful RA Guard
When there’s a stateless Router advertisement guard one might think there is also a stateful advertisement guard. And there is. It’s built through a defined policy with match conditions which inspects Router Advertisement messages containing information/attributes like address provisioning (slaac/dhcpv6), prefix delegation, neighbor detection.
At first an interface or vlan is places in learning state and records (snoops) the valid IPv6 routers. If no valid IPv6 router is attached it will dynamically transition into the blocking state.
In diagram form the functionality can be shown like this:
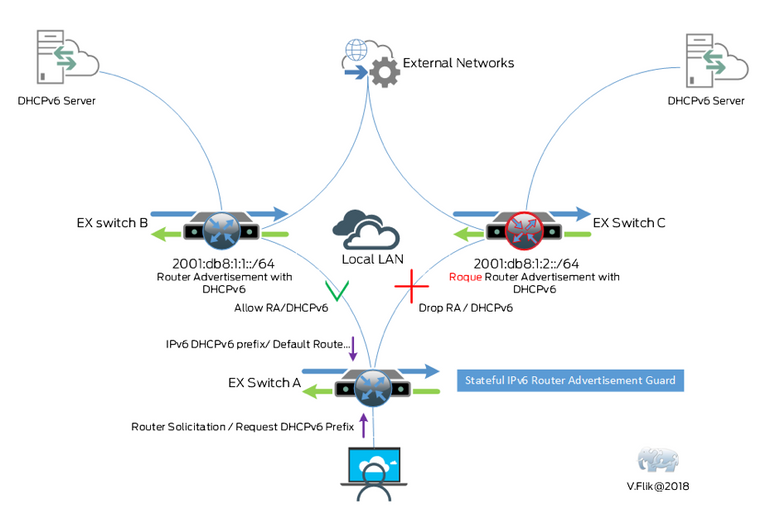
This feature is described very clear in the documentation.
Neighbor Discovery Inspection
Neighbor discovery inspection in IPv6 compares a little bit to Dynamic Arp Inspection in IPv4. It functions in combination with stateful address configuration. As soon as you enable this feature IPV6DHCP snooping is enabled (on ELS config style switches) and a DHCPV6 snooping table is built. ND traffic is validated against this table. So, whenever a spoofed address is used it comes in on a wrong port and the ND packet is dropped by the switch. Let’s again make it clear with a diagram: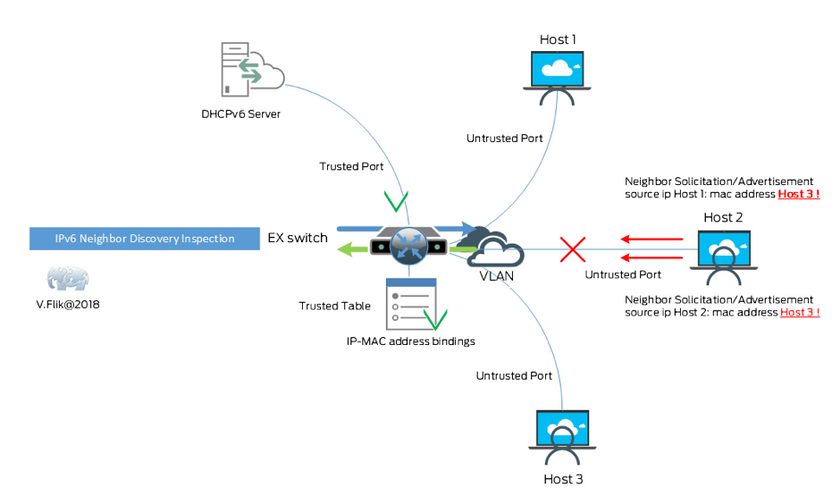
Once again a link to documentation on how to enable this feature.
And the last feature I’ll discuss is really very cool!
Secure Neighbor Discovery
In the “normal” Neighbor discovery process we just trust the communication between two neighbors. When the communication gets compromised or corrupted that goes by unnoticed. To solve this (without the need for ipsec ) a rfc (3971) is written to secure the communication with digital signatures. It looks to me like this feature is platform dependent, a good reason for you to visit the Feature Explorer. I did that and only found (v)SRX for this feature. Yet another diagram explains things:
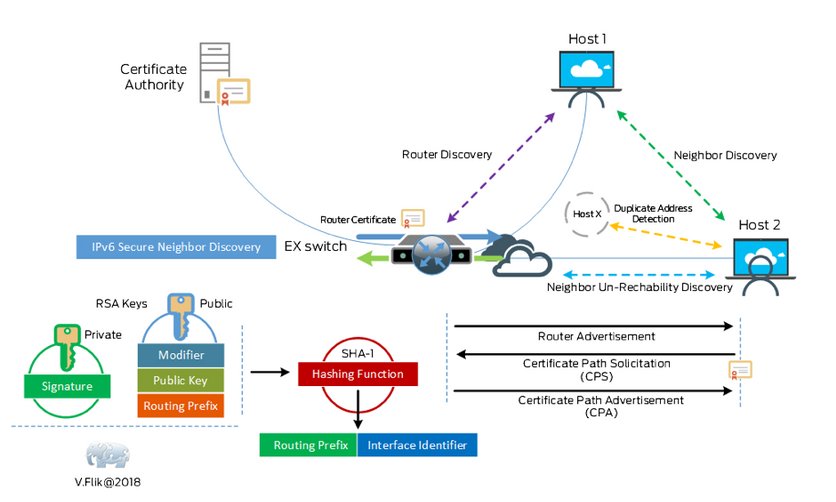
To enable this feature follow the instructions provided here.
All features discussed are on the IP layer (IPv6). To read about security on l2 (ethernet) please read my blog from 2013, I’m to lazy to write the same thing all over again. You can find it here.