
Background
Offering virtual form factor of firewalls, and supporting them in different clouds (like AWS, Azure etc) is not sufficient to claim seamless solution for multicloud deployments. Equally important is the need to support the policy and operational workflows to make multicloud deployments successful.
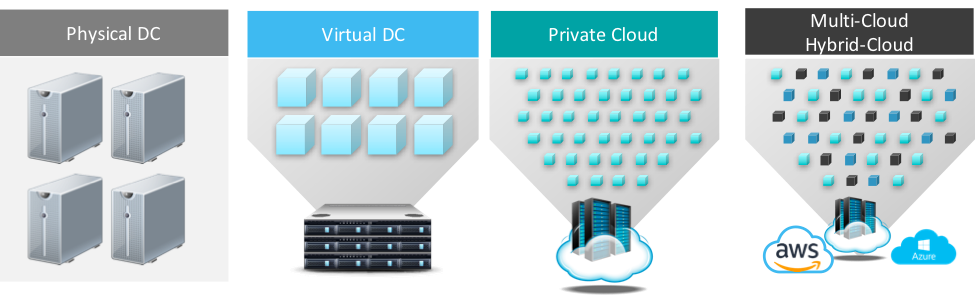
Three key trends below capture succinctly the developments in the application world:
- Application Architecture: Architectural transformation from complex, monolithic applications, to client-server applications, to 3-tier web applications (Web, App, DB tiers) to the current micro-services architecture involving a large number of much smaller “micro-services”. This trend enables smaller development teams to specialize in and deliver high quality micro-services thereby increasing the reliability and reuse of components across multiple applications.
- Application Deployment: Application deployment options transitioning from hardware oriented deployments to virtualized deployments which do not involve procuring and provisioning hardware for each application component, to private cloud oriented deployments, to multicloud deployments. Drivers for this trend include agility, elasticity of applications, as well as improved cost efficiencies
- Automation: Automation is becoming more and more prevalent. Continuous integration/delivery frameworks to accelerate application life cycles, application templates and blue prints to be able to instantiate cloud applications on a cookie-cutter basis and DevOps models to accelerate operational life cycles
Let’s see how these trends are putting significant strain on the enterprise IT (in particular security) teams.
Challenges
Operational processes established by the IT teams in majority of enterprises are based on the Physical/Virtual DC models optimized for limited number of well-defined applications that can be curated and managed well by a small team of IT administrators. 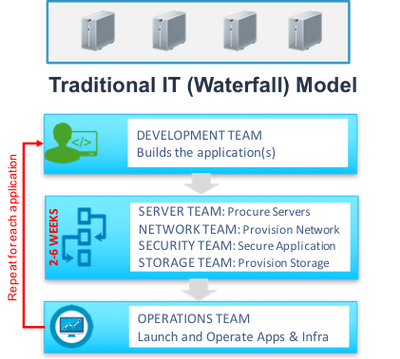
Reality in the new world data centers is quite different from what the original operational processes were designed for. For example:
- Agility: Traditional IT processes involved multiple weeks of IT security team testing, validation and risk mitigation before deployment of applications. This model is a complete non-starter in the cloud oriented world where the expectations are that the applications can be launched in a matter of few minutes – not a few weeks.
- Scale: As the number of network connected components increase exponentially with the cloud oriented and micro-services models, it is impossible for the resource constrained IT teams to curate all applications.
- Multi-location: As applications get hosted on-premises or in any of the public cloud locations, trying to come up with and maintain different security policy rules for the different domains, and go through audit and compliance separately adds significant operational overhead to the security teams which are already stretched thin.
Introducing Juniper’s enhanced security policy model in this blog that enables IT/security teams not compromise on the security of the applications as they drive hard towards the agility expectations in the cloud solutions.
Juniper solution – Security Director and SRX
Juniper Security Director, with its latest 17.2R1 release, introduced the ability to build “meta-data based policies” in order to address above challenges.
This feature enables security teams to:
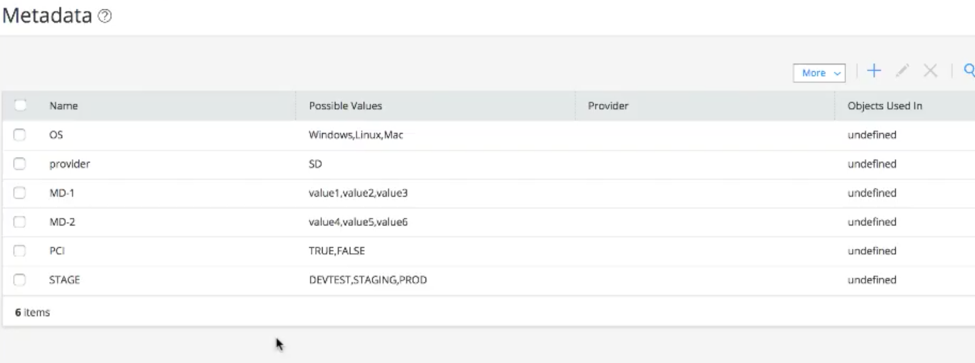
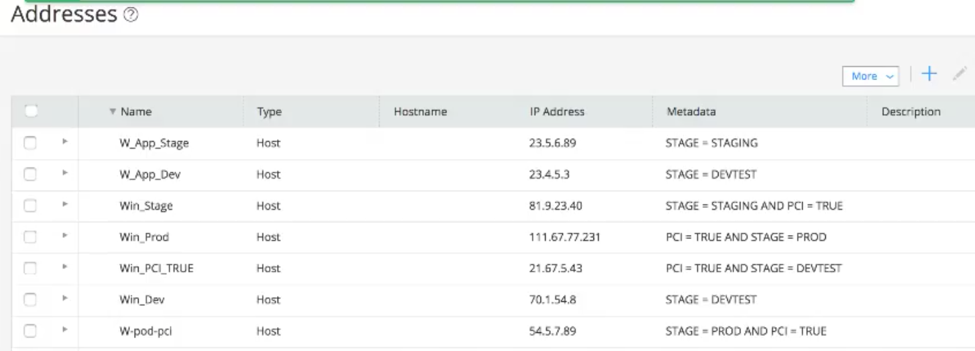
- Define custom meta-data: Meta-data is a set of strongly typed name – value pairs that can be applied for any network addressable entity. For example, customers can choose to use custom attributes like “Deployment_Status (DevTest, Staging or Production)”, “App_Tier (Web, App, DB)”, “PCI_Data (False, True)” and such for each of the network addressable entities. See Screenshot-1 below
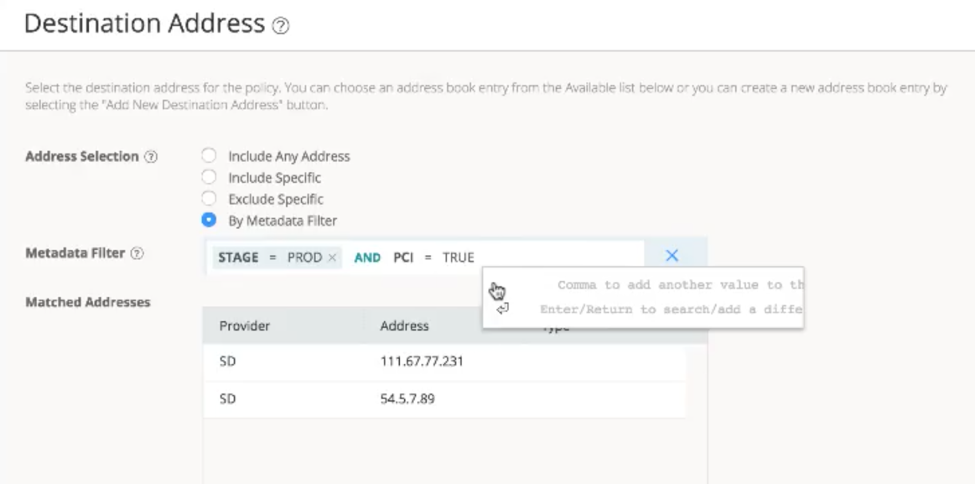
- Create flexible security policies based on meta-data: Create security policies, review, test and certify for compliance these policies. The criteria for the source and destination matching could now be based on logical expressions related to meta-data. For example, “App_Tier=DB AND PCI_Data=True” automatically match all data bases in the system that are tagged to have PCI related data. See Screenshot-2 below
- Deploy these policies to SRX firewalls: Deploy the approved policies to the SX firewalls ahead of the cloud application launch life cycle. If the source or destination match criteria is based on meta-data mapping, those elements get translated as SRX Dynamic Address Groups.
- Assign meta-data to new application components: At the time of the cloud application launch, assign right meta-data to the network components. Security rules on the SRX firewalls get auto-updated with the new application components such that right security rules are automatically in place on the relevant firewalls at the time applications connect to the network. See Screenshot-3 below
Of course, all these actions can be performed either through Security Director User Interface or through REST API. Following screenshots from Security Director illustrate above workflows:
Screenshot-1: Custom Meta-data in Security Director
Screenshot-2: Using Meta-Data in Security Policies
Screenshot-3: Assigning Meta-Data to Network Objects
Customer Benefits
Benefits of the above model as supported by Juniper are:
- Address Agility Requirements: The above approach makes sure that the security policy as defined by the security team is instantiated on the firewalls (based on steps 1 through 3 above) even before the applications and application components are created. As new application components get instantiated (step 4 above), the relevant firewall policies get auto updated with the meta-data mappings for the applications components and thereby automatic policy enforcement at the time of launch. Unless the rules themselves are changed, security administrators do not need to manually commit changes related to meta-data mapping of addresses.
- Address Multicloud Policy: As the application components get deployed inside the data center, or in different public cloud locations, it is possible to leverage the same security policy and deploy it to different SRXs or vSRXs in different locations and achieve consistent security posture.
- Single pane of glass: Security Director can now be leveraged to manage security policies of workloads irrespective of where the workloads are located. In addition, consistent security logging, monitoring and reporting features are supported to reduce the operational burden of managing different domains as independent islands of management
- As an additional bonus, security administrators can now get to see a more holistic picture about each network entity based on the meta-data assignments. They are no longer limited to having to make sense of the network entity just based on just the IP address of the entity.
Summary
It can clearly be observed from the above description that Juniper Security Director’s new meta-data based policy model enables security administrators achieve the security goals of the organization without becoming the bottleneck for the agility and scale requirements common in multicloud deployments
References
Solution Brief: Provides a more in-depth coverage about the solution, and applicability for multicloud deployments
Demo Video: Provides a quick demo of the solution
Dynamic Policy Actions Blog: Discusses a related but independent innovation in the security policy space focused enabling dynamically changeable security policy actions