Special thanks to Asher Langton, Peter Gael, Laurence Pitt, and Lee Fisher for their assistance in this rapid response.
[Update as of May 13th]
Microsoft has just released a public bulletin along with patches for Windows XP, Windows 8, and certain server platforms that did not receive the original MS17-010 update.You may view their announcement in full here.
Additionally, we've seen a new variant of WannaCry that does not leverage the original killswitch mechanism. Researchers currently suspect that this mechanism was an attempt at bypassing certain types of dynamic-analysis engines that automatically reply to arbitrary GET requests, thus preventing detonation within the environment and avoiding detection.
[Update as of May 15th]
WannaCry continues to evolve with multiple variations now propagating across the Internet. The vast majority of them still contain the original Sandbox evasion technique, albeit they point to new unregistered domains. Researchers are currently analyzing and registering domains as they are identified, although there are variations without this particular mechanism that are not susceptible to the killswitch behaviour.
Based on research by @hackerfantastic, it appears as though the likelihood of receiving a decryption key is low should a user pay for decryption services. WannaCry authors have received (at the time of writing) in excess of $51,000 for their efforts.
-----------------------------------------------------------------------------------------------
A new strain of self-replicating ransomware is affecting computers all over the world. It's known by various names: Wanna, WannaCry or Wcr. This malware is disrupting companies and services for businesses, governments, and consumers.
The information that we have at the time of this writing indicates that the initial point of infection within most organizations is via traditional mechanisms, primarily email and web-delivered PDF's sourced from the Necurs botnet. The novelty of WannaCry is its ability to break out from the initial “Patient Zero” and propagate laterally across an SMBv1-enabled network in rapid fashion.
The SMBv1 Unauthenticated Remote-Code-Execution (RCE) that has enabled WannaCry’s success was released in the recent ShadowBrokers dump on April 14th, 2017. It’s unofficially known as “EternalBlue” and was addressed preemptively by Microsoft on March 14th in the security bulletin MS17-010.
A look at one of the public examples of EternalBlue reveals why it’s so effective; it requires absolutely no interaction on the part of the attacker and facilitates an effective distribution mechanism for ransomware inside a vulnerable enterprise.
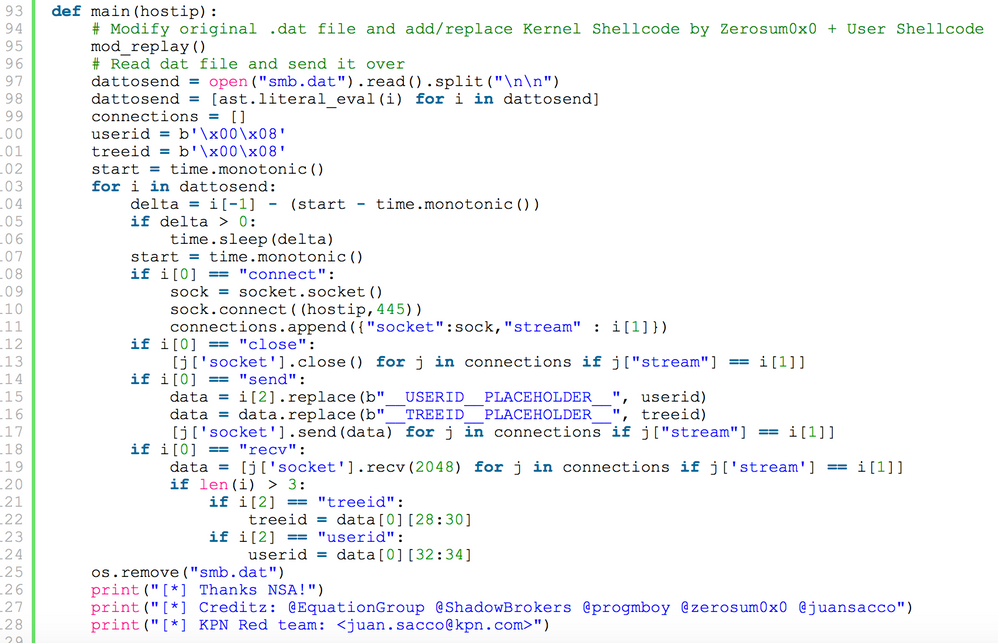 Credit to Juan Sacco for his PoC Code seen above (payload removed). Based on our analysis, it's highly probably that this code is being used directly by WannaCry
Credit to Juan Sacco for his PoC Code seen above (payload removed). Based on our analysis, it's highly probably that this code is being used directly by WannaCry
While Microsoft was proactive in releasing a patch for the SMBv1 issue (MS17-010), many users still have not deployed the fix, as can be evidenced by WannaCry's success. Also of note, no patch was released for Windows XP, which is still prevalently used in certain industries and geographies.
Juniper Protections
While the malware’s ability is concerning, Juniper security customers can rest easier that their environments remain protected. Below, we'll review the tools available to you today to ensure that an outbreak is prevented.
First and foremost, customers who have deployed our advanced anti-malware solution Juniper Sky ATP are very likely protected on multiple levels.
- Initial communication with the Necurs botnet is prevented via Sky ATP Security-Intelligence feeds. Inbound communication is dropped at the SRX firewall.
- If the network-based delivery mechanism is new or unique to you as a customer, the anti-malware portion of SkyATP will identify WannaCry using its robust inspection pipeline, made up of signature-based detection, machine learning-driven static analysis, and deceptive dynamic analysis (sandboxing). We’ve examined 24 unique samples as of May 12th and all have been caught within 30 seconds.
- Assuming Sky ATP did not block the file outright upon download, Sky ATP is designed to identify the new file as malicious and propagate this information to the on-premises SRX device, which in turn will quarantine the malware at the network level.
 WannaCry Ransomware identified within Juniper Sky ATP.
WannaCry Ransomware identified within Juniper Sky ATP.
 Behavioural Analysis Report of WannaCry within Juniper Sky ATP.
Behavioural Analysis Report of WannaCry within Juniper Sky ATP.
Customers who have deployed Juniper’s Secure Analytics (JSA) solution are well equipped to defend against many types of ransomware. In the specific case of WannaCry, the SIEM will generate multiple events and offences based on anomaly detection (peer-to-peer SMB and file-generation activities in particular).
As an example, JSA is able to detect abnormal file-write behaviour on a Windows 7 device that’s indicative of ransomware attacks:
 Generic Ransomware Detection within JSA
Generic Ransomware Detection within JSA JSA's Anomaly detection information.
JSA's Anomaly detection information.
You can see above that the offence was generated due to generic ransomware behaviour. When an endpoint begins to write large amounts of files (in this case, encrypt the entire filesystem), it’s rather trivial for a SIEM to detect. What makes Juniper’s offering unique is its ability to propagate arbitrary threat information, through open APIs, across our Software-Defined Secure Networks (SDSN) solution, isolating the affected host from the rest of the network within seconds.
For Juniper SRX and IDP customers, MS17-010 is covered by multiple CVEs and their corresponding signatures. You should ensure the following IDP signatures are enabled in your environment.
Detailed Analysis
For those who are curious, here are some additional insights into WannaCry below.
While the delivery mechanism seems to vary between targets, most payloads involve some sort of portable executable (PE) embedded within a parent file type, generally a PDF.
In the sample PE below, you immediately notice a hardcoded password of 'WNcry@2ol7' that will allow you to open an embedded zip file:
 Hardcoded password of WNcry@2ol7.
Hardcoded password of WNcry@2ol7.
If you decompress the zip file, you are then presented with the text versions of a ransom message in multiple languages, as can be seen here:
 .zip with ransom message in multiple languages. At first glance, the embedded tasksche.exe's function appears to probe all logical drives connected to the target:
.zip with ransom message in multiple languages. At first glance, the embedded tasksche.exe's function appears to probe all logical drives connected to the target:
 tasksche.exe disassembled.
tasksche.exe disassembled.
Upon executing the malicious file, the malware reaches out laterally via SMBv1 (TCP 445) using EternalBlue and the user is presented with the following sequence as the malware begins to encrypt the local drives:
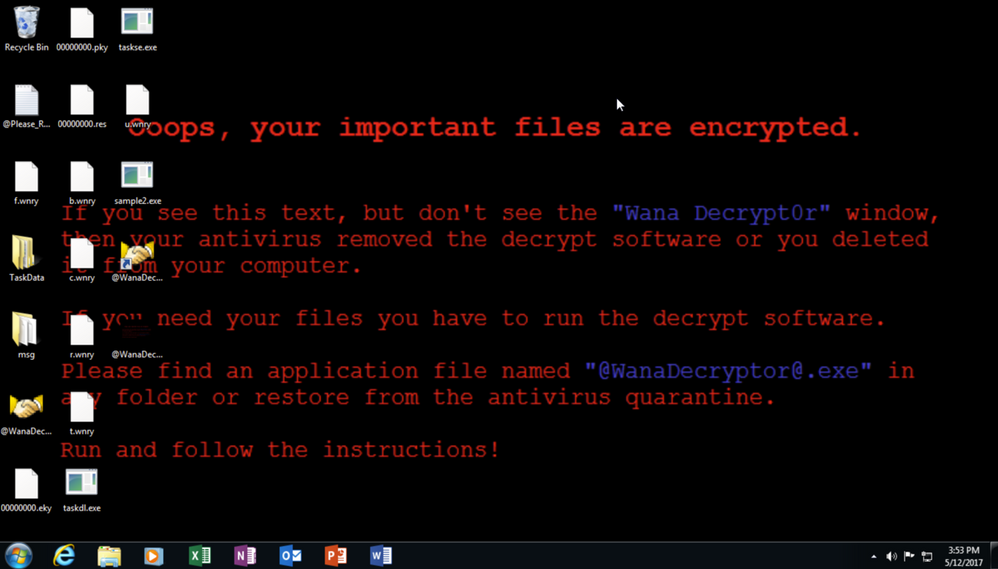
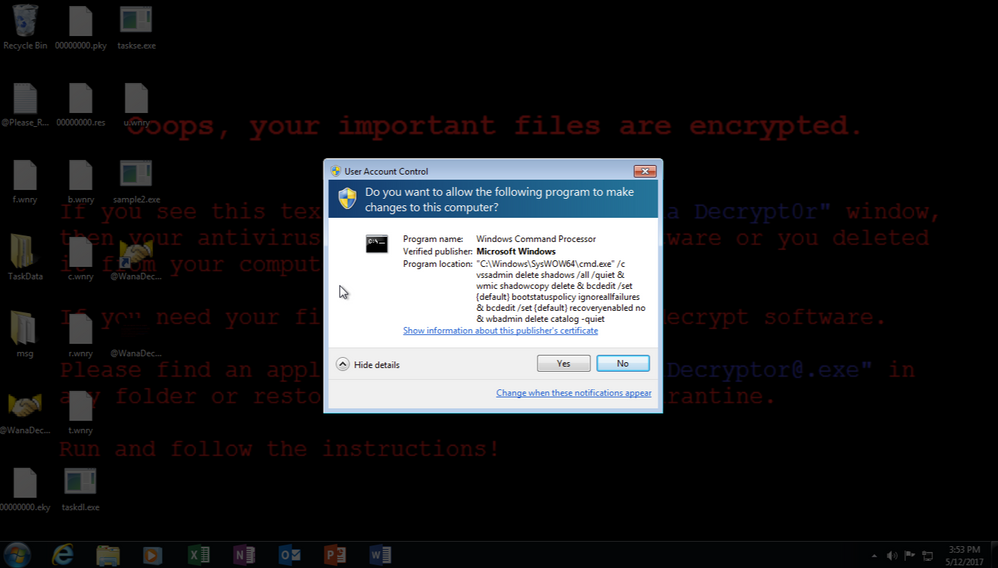
 And finally, the payment screen.
And finally, the payment screen.
Since the outbreak of the WannaCry ransomware researchers have been working hard to understand it’s spread and find a way to halt progress. At the time of this publishing, a security researcher who tweets as @MalwareTechBlog halted the spread by "accidentally" activating the killswitch, although the researcher admits that this could be temporary.
The assembly noted below generates a GET request (HTTP) for [uqerfsodp9ifjaposdfjhgosurijfaewrwergwea'.'com]. If the request fails, the malware continues to propagate as can be seen here: Credit to @darienhuss.
Credit to @darienhuss.
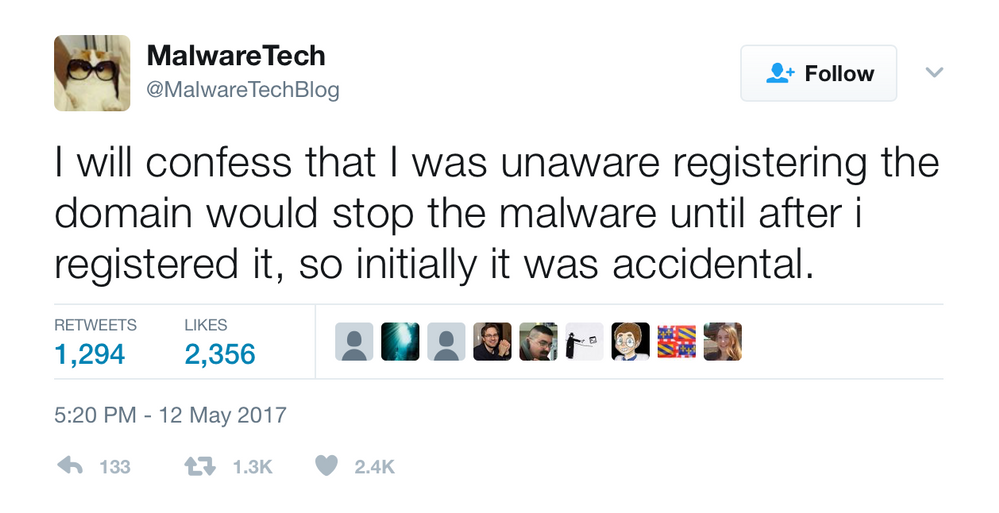
https://twitter.com/MalwareTechBlog/status/863187104716685312