This post was co-authored by Rakesh Kumar, Distinguished Engineer and Anil Lohiya, Principal Engineer of Juniper Networks.
************************************
At this year’s RSA event Juniper announced, “software defined secure networks” (SDSN). It has been the topic of discussion with customers and partners to make them think of security in a completely different way. This blog focuses on a new way of deploying security across the entire organization and cloud assets.
Before we embark on the journey to a software defined security model, let us first understand the traditional ways and what challenges they pose. In essence, let us answer a simple question of whether status quo is sufficient or a new paradigm is indeed the need of the hour.
This is one of the first blogs in a series where we will demystify and explain SDSN and what it takes to build this framework.
Traditionally, Enterprises focus their protection model on countering known and unkown external threats, coming from outside their organization. The external threats largely come in the form of malware or unauthorized access to data.
Once inside the enterprise, these threats could easily spread; where someone’s infected laptop or desktop could make Enterprise networks a botnet army and become a source of internal and external attacks.
In order to protect their network, Enterprises usually deploy multiple layers of siloed technologies that work independently of each other. Perimeter firewalls for example are often configured with all possible rules in an effort to prevent unknown malware, application and network attacks from penetrating the enterprise.
However, they don’t help in protecting against internal threats without complicated traffic hair-pinning – the result is previously unseen, new malware and attacks are left unchecked.
Another option for enterprises to protect against internal threats is to deploy multiple layers of firewalls, but that requires careful planning since it is difficult to take all internal traffic through a separate layer of firewalls.
This leads to the first challenge where internal threats are either not handled or partially handled through traffic hair-pinning manually.
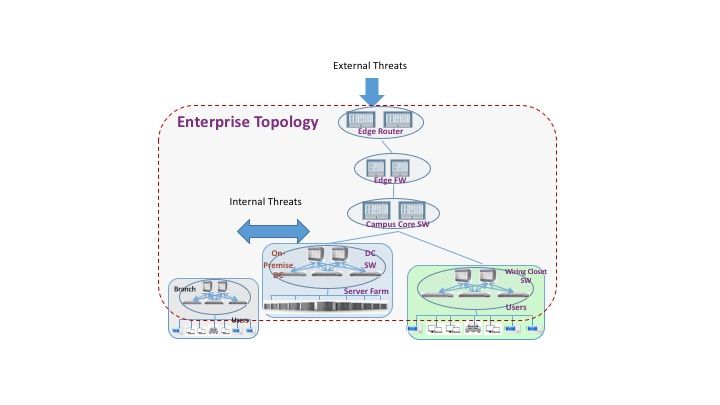
Figure 1: Enterprise Network Topology
In large Enterprises, there are usually multiple administrative domains for comprehensive security frameworks;
- There is a network security team that manages security policies on perimeter firewalls primarily to manage external threats.
- There is a network operations team, that typically manages security policies by using network and application isolation to protect against internal attacks and unauthorized access.
- Then there is third team, an IT team, that manages end-points such as laptops, desktops and application servers to make sure that they have the correct security posture.
The security framework in Enterprises become a highly fragmented approach due to multiple administrators, management systems and reliance on a lot of manual coordination among different admins and systems.
This leads to the second challenge where we lack a single pane of glass for security policy management and threat visibility.
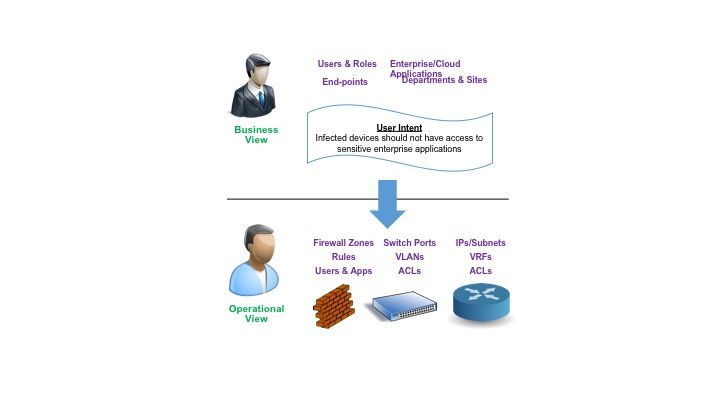
Figure 2: Security Provisioning Framework
Enterprises not only need to protect their information for pure business reasons but also have to comply with regulations. It becomes imperative that Enterprise Chief Information Security Officers (CISO) have very strong security policies.
But CISO’s don’t think of security policies as vendor device features, protocols, IP addresses and functionality, but rather think of security policies in a totally different way. They have users, roles, application & device assets, geographical sites and departments. They want to ensure that security policies implement proper access to resources and data based on business and regulatory needs.
This requires someone to understand the business requirements and translate them into vendor specific device configurations. Over time this becomes increasingly challenging as the number of rules explode and protection is needed against both internal and external threats.
To add to the challenge, Enterprise applications are deployed in hybrid clouds and the same consistent policies must be enforced independent of the location.
This leads to the third challenge where security policies cannot be configured based on business needs or user-intent.
As you can see the traditional model of security deployments are not sufficient in managing security risks in today’s Enterprise networks where threats are continually evolving and could emanate from anywhere.
In subsequent blogs, we will explain how Juniper’s SDSN solution take these challenges head-on and bring a new approach to security framework.
We want to acknowledge contributions from our colleague Lee Fisher.