The Internet has been one of the greatest revolutions in the history of mankind. By connecting computing resources around the world, Internet has created new ways for people to interact and work. Internet and the World Wide Web have been the platform of choice to build applications from banking and retail sectors to medicine and aeronautics. While most applications on the Internet are important for connectivity, it also brings with it an element risk. The World Wide Web is a source of threats in the form of malware and viruses. There are hackers trying to get in to corporates network and steal information. This makes it important for businesses to have a complete visibility of the usage patterns of the applications over the Internet accessed by their users. This visibility can help organization detect and block malicious or unauthorized network traffic.
In the 15.2 release of Junos Space Security Director, we introduced two new features to help network security adminstrators get better visibility in to their network. In this blog we will look at an overview of these two features.
Application Usage Statistics
The application usage statistics helps in better management of the network by definining application specified QoS, blocking application which are identified as malicious or unproductive. Security Director 15.2 supports in depth monitoring and reporting of applications used by users in the network. The information is presented using intuitive graphical representations, along with the detailed information in form of table and also in the form of PDF reports. A few screen shot, to illustrate the features, are shown below.
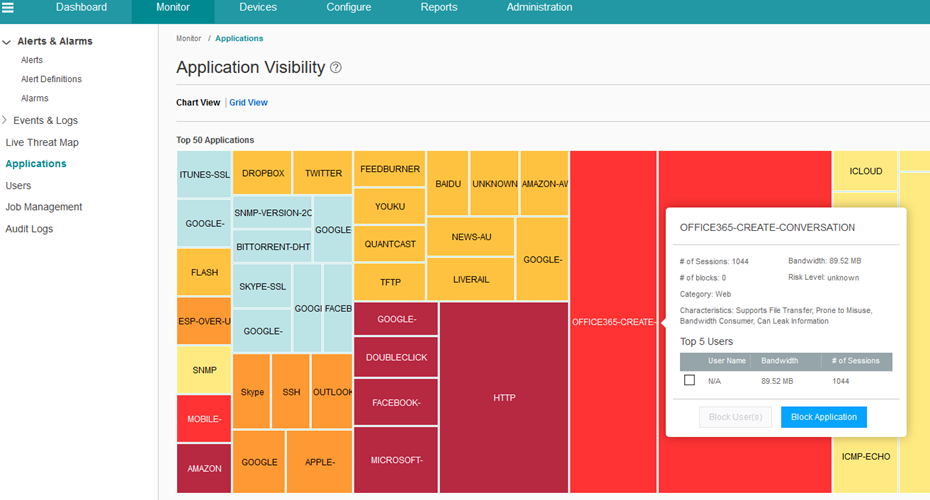
Screen 1 – The screen shot showing information about volume of data used by different application in network
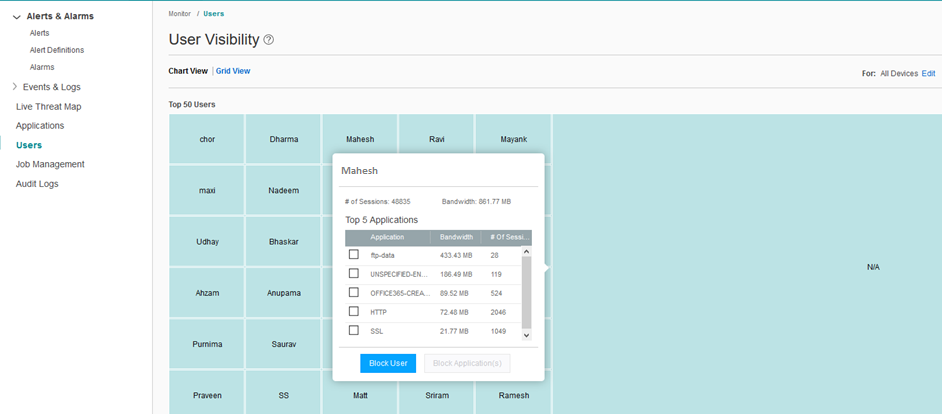
Screen 2 – Showing the screen of data used by each user, with details in tool tip
The Junos Space Security Director provides an interactive user interface to view the application usage information. The information can be viewed per application, category of the applications and their risk levels. The information can also be viewed per network user. The system allows the security administrators to generate a policy to block an application or a specific application for specific user and deploy the policy. The “screen 2” above shows how an action can be taken by the administrator, by selecting the applications that he wants to block for the selected user. In above screen, after selecting the application to block, administrator can click on the “Block User” to trigger the policy generation and publish/update workflow.
Junos Space Security Director presents a predefined report, which can be configured to run for different time periods allowing the administrator to generate a detailed application usage reports. The following screens show an example of the reports content.
 Screen 3 – Example content of the PDF Report
Screen 3 – Example content of the PDF Report
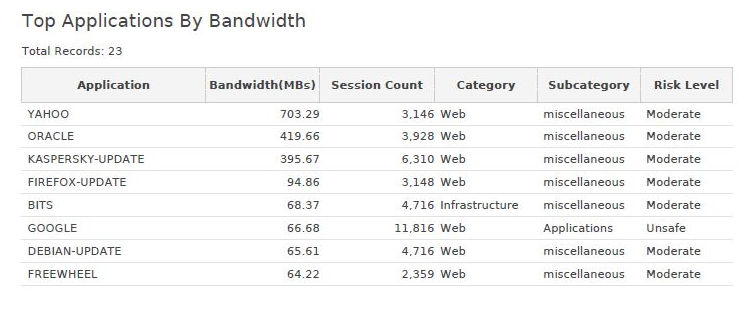
Screen 4 – Example PDF report content
The feature by default shows the overall usage of bandwidth in the network, without de-duplicating the data, if a same session passes through multiple cascade firewall. There is a device selection option, using which users can view the per-device application usage, for the configured zones on device, shown in the following screenshot.
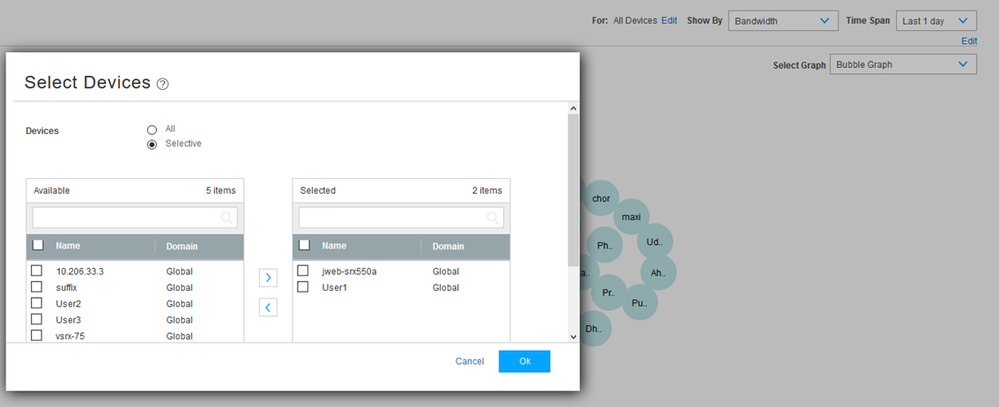 Screen 5 – Device Selection to choose and view data specific to a device
Screen 5 – Device Selection to choose and view data specific to a device
The application identification is handled by SRX devices, using the AppId feature. The SRX application identification gets triggered, if any of the four features that use the AppId is configured. The following four features trigger application identification on SRX platforms:
- Application Tracking
- Application Firewall
- Application QoS
- IDP
To understand more about these features on SRX, refer to the following link - http://www.juniper.net/techpubs/en_US/junos12.1/topics/concept/services-application-identification-application-package-understanding.html
The application visibility in Junos Space Security Director depends on the application tracking information sent by the SRX. The application tracking on SRX gets enabled per zone. When a zone has a configuration to enable AppTrack, SRX sends syslog messages about the application identified and the volume of data used by application for all the traffic going through the zone.
The syslogs sent by SRX are received and stored by Log Collectors (a part of Junos Space Security Director). The information from the syslogs is aggregated and stored in the MySQL database. This allows the Junos Space Security Director to store the application statistics for longer periods of time. This long term storage of application statistics information helps in generating application usage reports over period of months.
Junos Space Security Director also needs the application signature database installed (on Junos Space Security Director) to generate detailed information about the applications, and for appropriate classification of risk levels and application categories.
Threat Map
The new Junos Space Security Director also introduces the ability to visualize threats on the World Map. It is useful to security administrators in visualizing the geo location of origins of major threats in their network. The administrators are assisted with information that help them utilize advance security features and block malicious traffic based on the region of origin. Upon clicking a country or region the information specific to that region is shown. The system lets the user to further drill down, by allowing them to go to the event viewer, where they can see the filtered list of events that has been reported.
 Screen 6 – Threat shown on the world map, with their origin and destination
Screen 6 – Threat shown on the world map, with their origin and destination
The map shows the following 4 types of attacks information.
- IDP Detected Attacks - these are the attacks detected by the IDP module in the SRX. The information reported about these kinds of attacks are:
- Source of Attacks
- Destination of attacks
- Type of attack
- Session information
- Severity of the threat
- Policy information which permitted the traffic
- Action taken, either the traffic was still permitted or dropped
- Viruses detected by antivirus engine on SRX - the viruses can be detected from a file downloads in the network. The information reported are
- Source of the infected file
- Destination
- Name of the file name which was infected
- URL if any which was used for accessing the files
- Email spam – these threats are detected by SRX based on the blacklists. The reported information is:
- Source of the Space
- Action Taken, email was rejected or allowed
- Reason for identifying as spam
- Firewall authentication failure - If there are unauthorized attempts to access the section of network the Firewall Authentication messages are triggered. The reported information contains:
- Reason for authentication failure and source where the request came from.
You can download the latest version of Junos Space Security Director at - http://www.juniper.net/support/downloads/?p=spacesecdir
References
1. Configure Integrated User Firewall Using Junos Space Security Director
2. Juniper SRX firewall by Brad Woodberg and Rob Cameron online edition http://chimera.labs.oreilly.com/books/1234000001633/ch12.html#application_identification