What is a Trusted Platform Module (TPM)?
 Many new tablets, laptops and servers are now equipped with a small security chip called a Trusted Platform Module, or TPM, specified by an industry consortium called the Trusted Computing Group (http://www.trustedcomputinggroup.org). A number of vendors make inexpensive, self-contained TPMs, and some are starting to embed TPMs in larger processor chips, making the technology easily accessible. TPM technology is now starting to appear in embedded systems such as networking equipment.
Many new tablets, laptops and servers are now equipped with a small security chip called a Trusted Platform Module, or TPM, specified by an industry consortium called the Trusted Computing Group (http://www.trustedcomputinggroup.org). A number of vendors make inexpensive, self-contained TPMs, and some are starting to embed TPMs in larger processor chips, making the technology easily accessible. TPM technology is now starting to appear in embedded systems such as networking equipment.
TPMs have a wide variety of uses, all of which guard the integrity of the host platform, but there are several that are most commonly implemented:
- The TPM can be used to provide assurance that the software system that booted on a processor is the one that the administrator of the systems wants there, and that it has not been hacked. This process is often called “Measured Boot” (more on that in a moment...)
- The TPM can store secrets of various sorts, usually cryptographic keys. The TPM API is defined to provide restricted access to the stored secrets, and TPM hardware is often designed to be tamper-resistant, so that hackers can’t gain access, even with physical presence.
- The TPM can also store data that’s not secret, but must not be changed without authorization; public keys proving platform identity would be a common use-case, where the key is not secret, but it’s important that hackers not be able to change it.
- Finally, the TPM usually includes a Random Number Generator that can produce a stream of cryptographic-quality random numbers. This is a surprisingly difficult problem, so having a TPM as one source of “entropy” (the cryptographer’s name for truly random numbers) can be an important contributor to security.
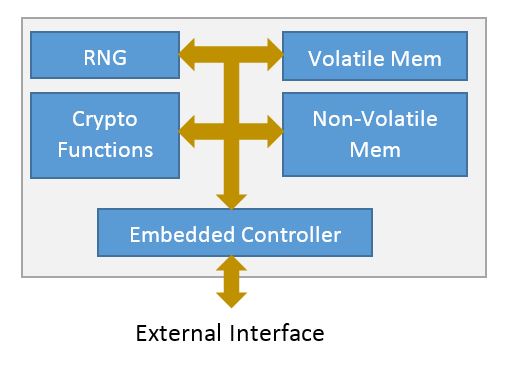 A discrete TPM chip is usually implemented as a small self-contained processor with additional logic for cryptographic operations such as RSA signing, key generation, random number generation, hashing and non-volatile storage, all carefully armored to thwart physical attacks. TPMs are not cryptographic accelerators; while they can be used for many kinds of tasks such as hashing and signing, the low power constraint (typically under a watt) and slow bus interface (Intel’s LPC or SPI are common) restrict operations to those that actually need to be kept isolated from the rest of the processor system.
A discrete TPM chip is usually implemented as a small self-contained processor with additional logic for cryptographic operations such as RSA signing, key generation, random number generation, hashing and non-volatile storage, all carefully armored to thwart physical attacks. TPMs are not cryptographic accelerators; while they can be used for many kinds of tasks such as hashing and signing, the low power constraint (typically under a watt) and slow bus interface (Intel’s LPC or SPI are common) restrict operations to those that actually need to be kept isolated from the rest of the processor system.
That doesn’t mean that a TPM can’t be used to secure high-throughput encryption... Applications that do full-disk encryption may use a TPM to store the symmetric key used by the disk encryption software on the platform; in that case, the TPM is programmed to release the symmetric encryption key only when the right conditions are met, for example, when the platform’s OS is in a known state, and the correct user password has been obtained. Only then will the TPM release the full-disk symmetric key, leaving the contents of the disk inaccessible if any of the required conditions are not met.
While the TPM has many mechanisms to guard secrets, ultimately we still depend on the host processor to use the secrets properly. To help ensure that the host processor is running known-good software, the TPM provides a facility called Platform Configuration Registers (PCRs) to implement Measured Boot. In TPM lingo, a Measurement is taken when the currently-running software element computes the hash of an about-to-be-run software module, as would happen, for instance, if a BIOS were to compute the hash of an OS Loader like GRUB2 (https://wiki.gentoo.org/wiki/GRUB2) before launching it. In a Measured Boot system, each stage of the boot process measures the next stage, and before launching it, stores the hash in a TPM by causing the new value to be hashed with whatever was already in one of the PCRs. Since the TPM won’t allow the PCRs to be directly manipulated, by the time the boot sequence is done, the PCRs will contain unique values that give a fingerprint of each and every module loaded. A management station can check later and retrieved the PCRs (signed by a key unique to the TPM to prevent tampering) to verify what version of which package is running on the platform.
While a TPM may be physically a small addition to a computing device, it has the potential to make a huge difference to the security posture, reducing the chances of undetected malware, and making theft of secret keys much more difficult.