Hello everyone,
i'm getting ready for the JN0-333 exam. i have made a GNS3 lab to see how a route-based IPsec VPN works. following you can see my network topology:
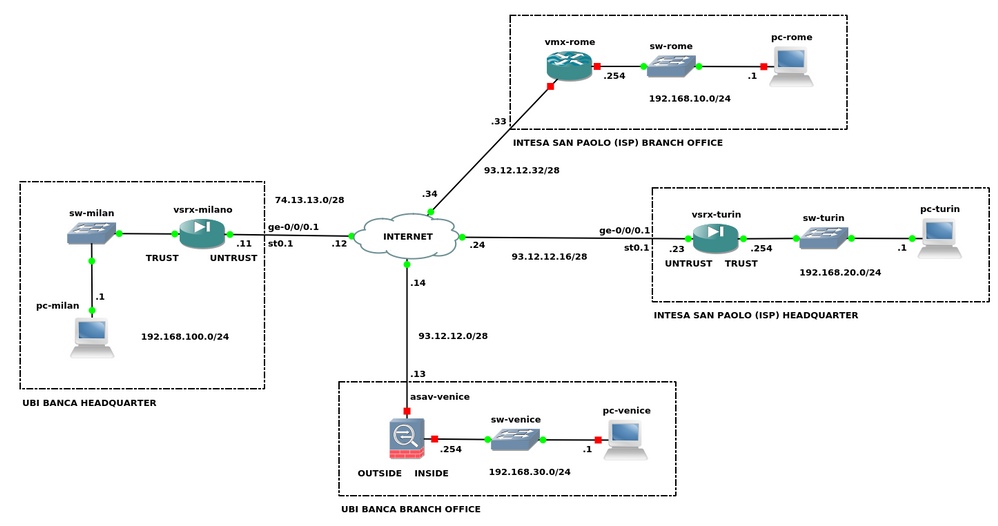
i would like to configure a point-to-multi point IPsec VPN using OSPF as the routing protocol. i want to build a hub and spoke network, with the vsrx-milan as the hub for the branch and non-branch remote sites. but before to do this I need to see implementations a little easier, like a simple site-to-site IPsec VPN.
currently i just configure a point-to-point IPsec VPN between Milan and Turin sites. I have used static routes for the routing and none IP address for the st0.1 interfaces. you can see my configurations in the attachments. i see the ike phase 1 and 2 tunnel up and working:
root@vsrx-milan> show security ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
5856949 UP 96b1ec76aeece4a1 83993bda88bfb67f Main 93.12.12.23
root@vsrx-milan>
root@vsrx-milan> show security ipsec security-associations
Total active tunnels: 1
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<131073 ESP:aes-cbc-256/sha1 6ea3f868 3567/ unlim U root 500 93.12.12.23
>131073 ESP:aes-cbc-256/sha1 83805b5e 3567/ unlim U root 500 93.12.12.23
root@vsrx-milan>
root@vsrx-milan> show security ipsec statistics
ESP Statistics:
Encrypted bytes: 608
Decrypted bytes: 336
Encrypted packets: 4
Decrypted packets: 4
AH Statistics:
Input bytes: 0
Output bytes: 0
Input packets: 0
Output packets: 0
Errors:
AH authentication failures: 0, Replay errors: 0
ESP authentication failures: 0, ESP decryption failures: 0
Bad headers: 0, Bad trailers: 0
root@vsrx-milan>
but, if the tunnel is up and the security policies are ok, why the pc-milan can't make a telnet to reach the pc-turin? note: pc-milan and pc-turin are the cisco routers and their routing is ok. it's the same for the INTERNET cloud.
pc-milan#telnet 192.168.20.1
Trying 192.168.20.1 ...
% Connection timed out; remote host not responding
where i'm going wrong?